Prisma Certified Cloud Security Engineer
Last Update 1 day ago
Total Questions : 250
PCCSE is stable now with all latest exam questions are added 1 day ago. Just download our Full package and start your journey with Paloalto Networks Prisma Certified Cloud Security Engineer certification. All these Paloalto Networks PCCSE practice exam questions are real and verified by our Experts in the related industry fields.
You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public cloud account and immediately see all of the alerts associated with this account based off ALL of your tenant’s existing enabled policies. There is no requirement to send alerts from this account to a downstream application at this time.
Which option shows the steps required during the alert rule creation process to achieve this objective?
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
What must be created in order to receive notifications about alerts generated when the operator is away from the Prisma Cloud Console?
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
In WAAS Access control file upload controls, which three file types are supported out of the box? (Choose three.)
Given the following audit event activity snippet:
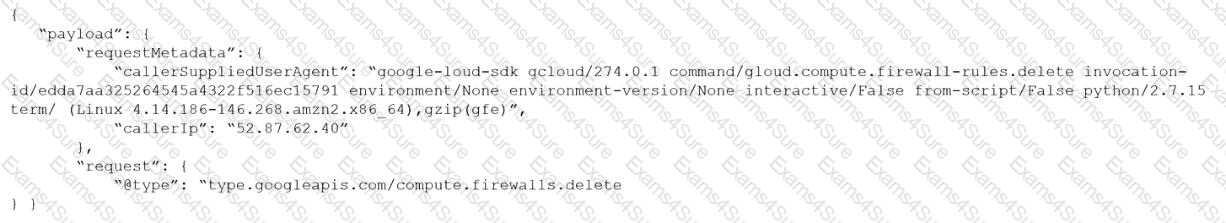
Which RQL will be triggered by the audit event?
A)
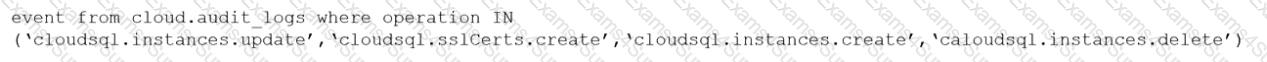
B)

C)

D)

Which file extension type is supported for Malware scanning in Prisma Cloud Data Security (PCDS)?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
Which option shows the steps to install the Console in a Kubernetes Cluster?
You wish to create a custom policy with build and run subtypes. Match the query types for each example.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
What are the two ways to scope a CI policy for image scanning? (Choose two.)
A manager informs the SOC that one or more RDS instances have been compromised and the SOC needs to make sure production RDS instances are NOT publicly accessible.
Which action should the SOC take to follow security best practices?
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
Which type of query is used for scanning Infrastructure as Code (laC) templates?
Which of the following are correct statements regarding the use of access keys? (Choose two.)
Which statement accurately characterizes SSO Integration on Prisma Cloud?
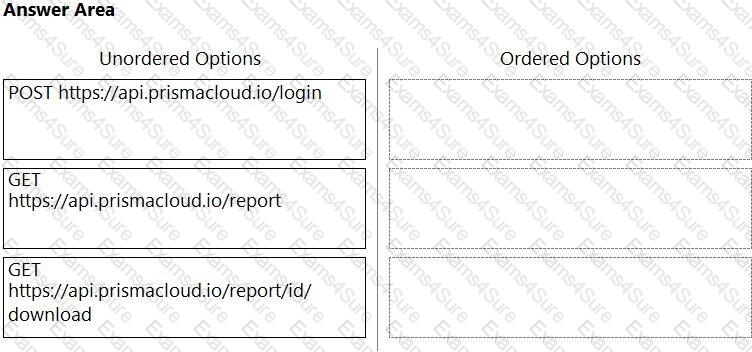
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
One of the resources on the network has triggered an alert for a Default Config policy.
Given the following resource JSON snippet:
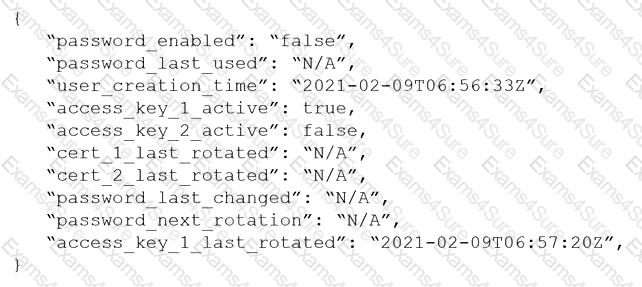
Which RQL detected the vulnerability?
A)

B)

C)

D)

Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
Which API calls can scan an image named myimage: latest with twistcli and then retrieve the results from Console?
Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
Which categories does the Adoption Advisor use to measure adoption progress for Cloud Security Posture Management?


TESTED 25 Apr 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.