Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
Last Update 1 hour ago
Total Questions : 380
Dive into our fully updated and stable 350-401 practice test platform, featuring all the latest CCNP Enterprise exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our free CCNP Enterprise practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 350-401. Use this test to pinpoint which areas you need to focus your study on.
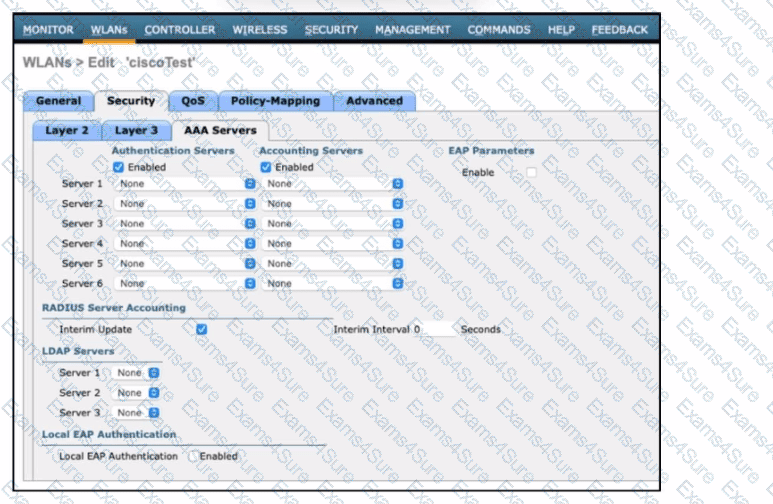
Refer to the exhibit. An engineer must configure a Cisco WLC with WPA2 Enterprise mode and avoid global server lists. Which action is required?
Which mechanism is used to protect the confidentiality of sensitive information exchanged over REST APIs?
Which task Is mandatory when provisioning a device through the plug-and-play workflow in Cisco DNA Center?
Which lag/profile on a Cisco Catalyst 9800 Series WLC must be modified to allow Cisco ISE to dynamically assign VLANs to users on an 802.1X-based SSID?
In a wireless network environment, which measurement compares the received signal to the background noise?
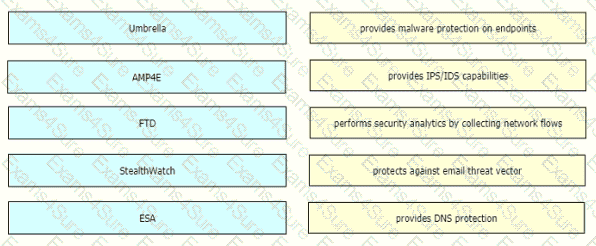
Drag and drop the threat defense solutions from the left onto their descriptions on the right.
Which two nodes comprise a collapsed core in a two-tier Cisco SD-Access design? (Choose two.)
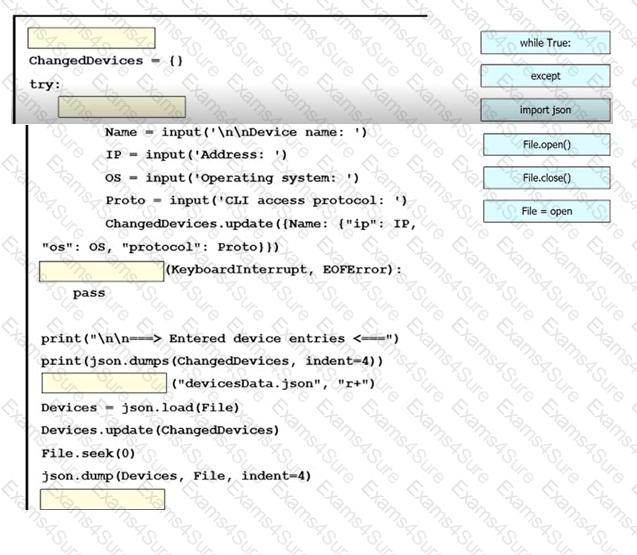
An engineer must create a script to append and modify device entries in a JSON-formatted file. The script must work as follows:
Until interrupted from the keyboard, the script reads in the hostname of a device, its management IP address, operating system type, and CLI remote access protocol.
After being interrupted, the script displays the entered entries and adds them to the JSON-formatted file, replacing existing entries whose hostname matches.
The contents of the JSON-formatted file are as follows

Drag and drop the statements onto the blanks within the code to complete the script. Not all options are used.


TESTED 18 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.