CompTIA A+ Certification Core 2 Exam
Last Update 2 days ago
Total Questions : 845
Dive into our fully updated and stable 220-1102 practice test platform, featuring all the latest A+ exam questions added this week. Our preparation tool is more than just a CompTIA study aid; it's a strategic advantage.
Our free A+ practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 220-1102. Use this test to pinpoint which areas you need to focus your study on.
Which of the following device types would a technician consider a security concern?
A proxy server is required for internet access from a corporate network. Which of the following should a technician perform to manually configure a Windows 10 device for internet access?
A user is unable to access the company's network. A technician learns the user's account became inaccessible after multiple unsuccessful login attempts. The user also changed their password before the issue started. Which of the following steps should the technician take to resolve the issue?
A hard drive that previously contained PII needs to be repurposed for a public access workstation. Which of the following data destruction methods should a technician use to ensure data is completely removed from the hard drive?
A technician recently installed a new router for a small business. Afterwards, the technician completed an external port scan and generated the following information:
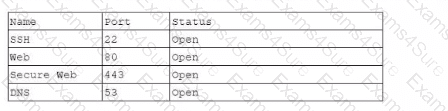
Which of the following should the technician perform next in order to follow best practices?
The Chief Executive Officer at a bank recently saw a news report about a high-profile cybercrime where a remote-access tool that the bank uses for support was also used in this crime. The report stated attackers were able to brute force passwords to access systems. Which of the following would best limit the bank’s risk? (Select two).
A technician is adding some Windows 10 workstations to the corporate domain. A script was able to add the majority of the workstations, but failed on a couple. Which of the following menus should the technician check in order to complete the task manually?
A small company has an office in a multitenant building. The company has implemented a wireless network for its employees to use. However, the network speeds are slow, and many employees have had intermittent access to the Internet. The network consists of a single wireless router with default settings in place. Which of the following should a technician do to improve the network speed and Internet access?
A technician is troubleshooting an issue on a PC that has low disk space. Which of the following Control Panel utilities should the technician most likely use to investigate and remediate the issue?
A technician ran the following command on a user's workstation:
net use G: \\server1\team\documents /persistent:yes
Which of the following did the technician set up by running this command?
A user has been adding data to the same spreadsheet for several years. After adding a significant amount of data, they are now unable to open the file. Which of the following should a technician do to resolve the issue?
A company executive is currently attending a major music festival with a large number of attendees and is having trouble accessing a work email account. The email application is not downloading emails and appears to be stuck during connection attempts. Which of the following is most likely causing the disruption?
Which of the following can be used for multifactor authentication when logging in to a computer system? (Select two).
Given the following information:
jdoe pizza
jdoe rock
jdoe guitar
Which of the following types of attacks is occurring?
A technician has been tasked with installing a workstation that will be used for point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
Which of the following applications allows a user to create backups in macOS?
A technician is configuring a workstation's security settings, and the following options are available:
Account lockout policy
Group policy
Two-factor authentication
Password complexity requirements
Firewalls
User accounts
Access control lists
Antivirus software
Which of the following settings should the technician configure to deploy strong password enforcement across the enterprise?
A technician is unable to connect to a user's workstation to troubleshoot an issue. The user is able to ping the IP address of the gateway. However, the technician is unable to ping the user's device. Which of the following workstation tools should the technician use to resolve this issue?
A user is unable to access the internet but can still print to network printers. Other users are not experiencing this issue. Which of the following steps should the technician take first to diagnose the issue?
A help desk technician is preparing to upgrade the company's desktop OS from Windows 7 to Windows 10. The technician needs to ensure the upgrade will preserve the users’ applications and data but also minimize the time and effort required for the upgrade. Which of the following would the technician most likely do?


TESTED 03 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.