CompTIA CyberSecurity Analyst CySA+ Certification Exam
Last Update 2 days ago
Total Questions : 462
Dive into our fully updated and stable CS0-003 practice test platform, featuring all the latest CompTIA CySA+ exam questions added this week. Our preparation tool is more than just a CompTIA study aid; it's a strategic advantage.
Our free CompTIA CySA+ practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about CS0-003. Use this test to pinpoint which areas you need to focus your study on.
A company's internet-facing web application has been compromised several times due to identified design flaws. The company would like to minimize the risk of these incidents from reoccurring and has provided the developers with better security training. However, the company cannot allocate any more internal resources to the issue. Which of the following are the best options to help identify flaws within the system? (Select two).
Which of the following best explains the importance of playbooks for incident response teams?
A systems administrator receives reports of an internet-accessible Linux server that is running very sluggishly. The administrator examines the server, sees a high amount of memory utilization, and suspects a DoS attack related to half-open TCP sessions consuming memory. Which of the following tools would best help to prove whether this server was experiencing this behavior?
The analyst reviews the following endpoint log entry:
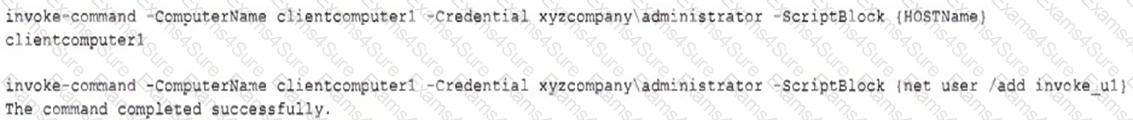
Which of the following has occurred?
A systems administrator needs to gather security events with repeatable patterns from Linux log files. Which of the following would the administrator most likely use for this task?
A corporation wants to implement an agent-based endpoint solution to help:
Flag various threats
Review vulnerability feeds
Aggregate data
Provide real-time metrics by using scripting languages
Which of the following tools should the corporation implement to reach this goal?
A systems administrator notices unfamiliar directory names on a production server. The administrator reviews the directory listings and files, and then concludes the server has been
compromised. Which of the following steps should the administrator take next?
A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization. Which of the following will produce the data needed for the briefing?
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
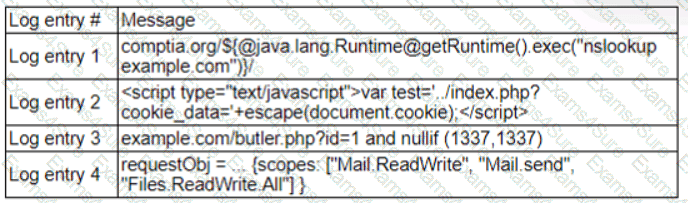
Which of the following log entries provides evidence of the attempted exploit?


TESTED 03 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.