|
|
Two Ways to Mastery: Learn with the PDF, Validate with the N10-009 Simulator. Know You're Ready and Pass with 100% Confidence. Your Complete CompTIA Network+ Success Package: Study Anywhere, Test Anywhere.

CompTIA Network+ Certification Exam
In Real Exam At Testing Centre
Exact Questions as in Real Exam Word by Word
CompTIA N10-009 Questions and Answers
A network administrator is in the process of installing 35 PoE security cameras. After the administrator installed and tested the new cables, the administrator installed the cameras. However, a small number of the cameras do not work. Which of the following is the most reason?
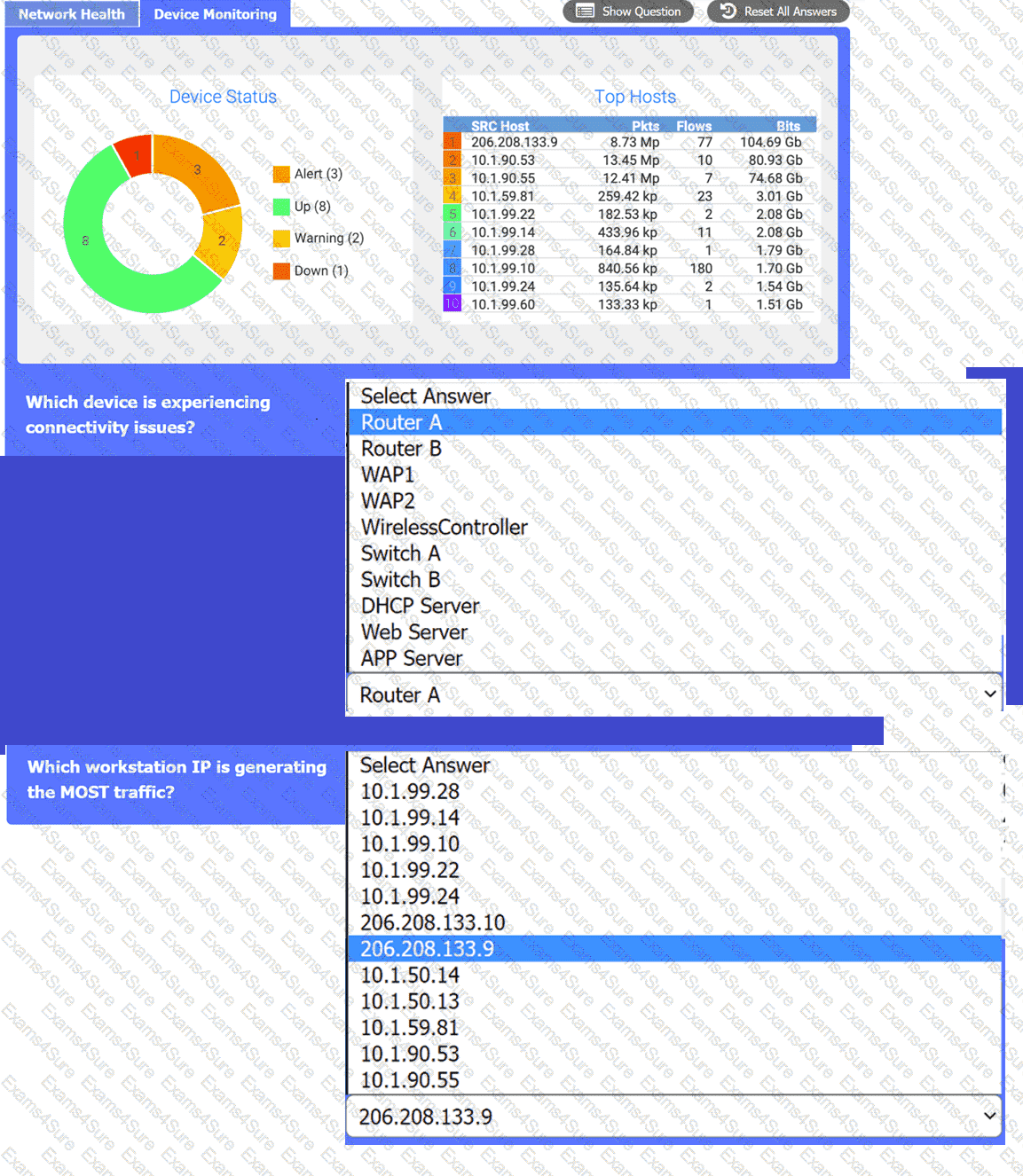
After a recent power outage, users are reporting performance issues accessing the application servers. Wireless users are also reporting intermittent Internet issues.
INSTRUCTIONS
Click on each tab at the top of the screen. Select a widget to view information, then
use the drop-down menus to answer the associated questions. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
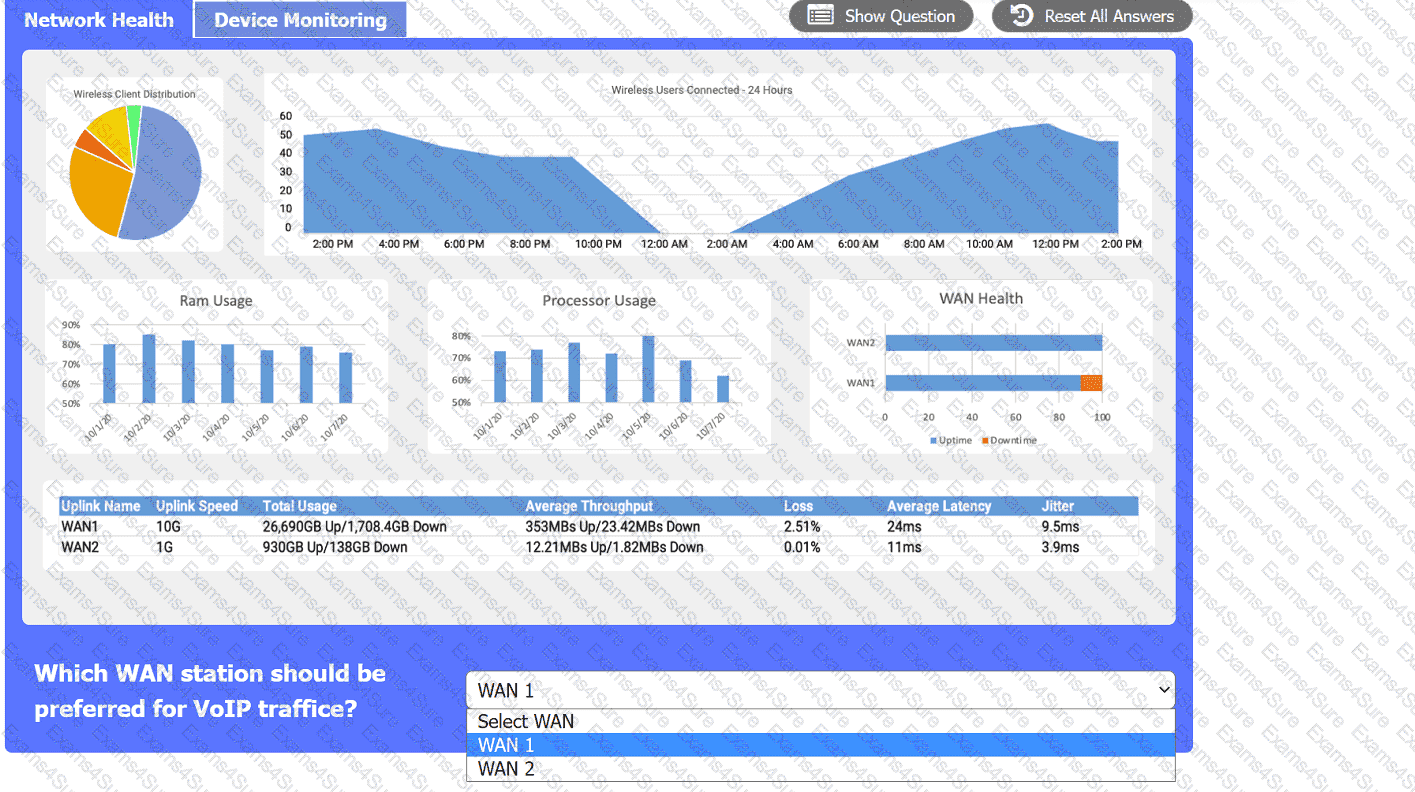
Employees report that the network is slow. The network engineer thinks the performance issue is with an upstream router. Which of the following tools should the engineer use to determine the location of the issue?
Latest and Up-to-Date N10-009 dumps with real exam questions answers.
Get 3-Months free updates without any extra charges.
Experience same exam environment before appearing in the certification exam.
100% exam passing guarante in the first attempt.
15 % discount on more than one license and 25 % discount on 10+ license purchases.
100% secure purchase on SSL.
Completely private purchase without sharing your personal info with anyone.
Are you preparing for the CompTIA Network+ N10-009 certification exam? Do you want to increase your chances of passing the exam on your first attempt? Look no further than our comprehensive Network+ N10-009 practice test.
Our practice test includes exam N10-009 answers and is designed to mimic the actual exam, allowing you to get a feel for the format and types of questions you will encounter. With our CompTIA Network+ N10-009 practice test, you can assess your knowledge and identify areas where you need further study, giving you the confidence you need to ace the exam.
Our CompTIA N10-009 exam dumps are up-to-date and regularly reviewed to ensure accuracy and relevance. We also offer a free N10-009 practice test, CompTIA Network+ N10-009 dumps and a Network+ N10-009 practice test PDF, making it easy to access the resources you need to succeed.
Stop the stress of unpredictable exam. Our N10-009 practice test is engineered to simulate the exact format, pacing, and pressure of the real CompTIA Network+ exam. Go beyond simple CompTIA Network+ Certification Exam exam questions and answers; practice with N10-009 exam dumps in an interface that mirrors the actual CompTIA test, building the muscle memory and confidence you need to pass on your first try.
Real Exam Simulation:
Our N10-009 practice exam interface is designed to look, feel, and function just like the real Pearson VUE testing software. From the timer countdown to the way you navigate between CompTIA Network+ Certification Exam exam questions, there will be no surprises on exam day.
Performance Analytics:
Get more than just a score. Receive a detailed breakdown of your performance by topic area. Identify your CompTIA Network+ certification weak spots and focus your study efforts efficiently.
Verified & Updated Questions:
Our team of CompTIA experts continuously updates the question bank to ensure all content is relevant, accurate, and aligned with the latest N10-009 exam objectives.
Interactive Learning:
Read the explanation for every answer right or wrong. Understand the why behind each concept to solidify your CompTIA Network+ Certification Exam knowledge, not just memorize a answer.
Build Exam Stamina:
Taking our full-length, timed N10-009 practice test builds the mental endurance required to maintain focus and performance throughout the entire CompTIA Network+ exam.
The CompTIA Network+ N10-009 certification exam is an industry-recognized certification for network technicians and engineers.
Our Network+ N10-009 practice test includes a comprehensive set of questions and answers designed to mimic the actual exam.
The CompTIA Network+ N10-009 practice test allows you to assess your knowledge and identify areas where you need further study, giving you the confidence you need to ace the exam.
Our CompTIA N10-009 exam dumps are regularly reviewed and updated to ensure accuracy and relevance.
We offer a free N10-009 practice test to help you prepare for the exam.
Our CompTIA Network+ N10-009 dumps include a comprehensive set of questions and answers designed to mimic the actual exam.
Yes, we offer a Network+ N10-009 practice test PDF, making it easy to access the resources you need to succeed.
The CompTIA Network+ N10-009 certification is valid for three years.
The Network+ N10-009 exam includes a maximum of 90 questions.
The passing score for the Network+ N10-009 exam is 720 out of 900.
The N10-009 introduces new concepts like emerging technologies, cloud, and virtualization, whereas the N10-008 focused more on foundational network infrastructure and operations. N10-009 is more updated with modern networking practices.
The N10-009 places greater emphasis on cloud computing and virtualization, addressing modern infrastructure trends and technologies.
The N10-009 gives more weight to security topics, particularly network security, threat management, and risk mitigation, reflecting the growing importance of securing modern networks.
Yes, N10-009 covers more advanced troubleshooting techniques and introduces tools for diagnosing cloud-based and virtualized environments, while N10-008 focused on traditional network performance issues.
Yes, N10-009 includes topics like SDN (Software-Defined Networking), edge computing, and IoT (Internet of Things), which were either minimally covered or absent in N10-008.
The N10-009 focuses more on modern network architectures, such as cloud and hybrid environments, while the N10-008 concentrated more on traditional LAN/WAN architecture.
Wireless networking is addressed in both exams, but N10-009 includes more on modern wireless technologies, such as Wi-Fi 6 and mesh networks, while N10-008 was more focused on earlier wireless standards.
N10-009 covers newer protocols and advanced routing protocols, while N10-008 focused more on traditional TCP/IP protocols and basic routing.
Yes, the N10-009 introduces network automation, scripting, and API usage, reflecting the growing importance of automating network management tasks.
The N10-009 places a stronger emphasis on cloud-based network configurations, compared to the N10-008, which mainly covered traditional on-premise networks.
Distribution uses hashing algorithms where Exams4sure is placed in our N10-009 study pack.


TESTED 09 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.