Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Last Update 2 days ago
Total Questions : 1237
Dive into our fully updated and stable 200-301 practice test platform, featuring all the latest CCNA exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our free CCNA practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 200-301. Use this test to pinpoint which areas you need to focus your study on.
Which value is the unique identifier that an access point uses to establish and maintain wireless connectivity to wireless network devices?
Refer to the exhibit.
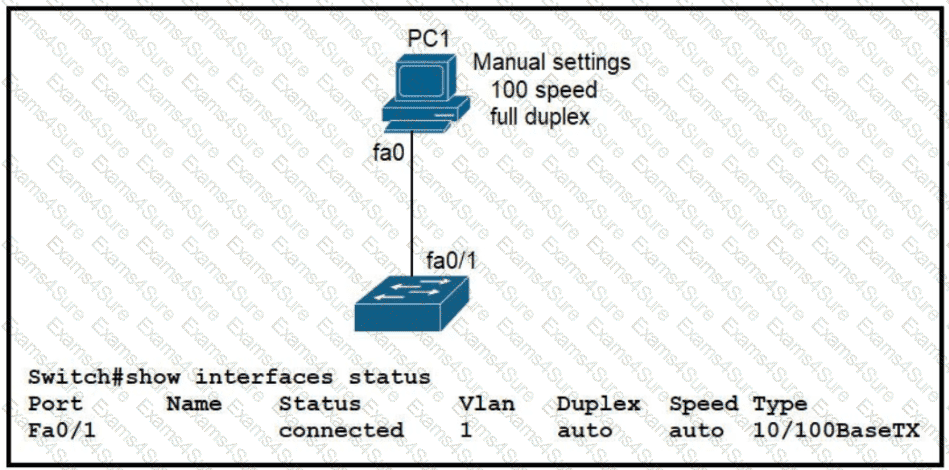
The link between PC1 and the switch is up. but it is performing poorly. Which interface condition is causing the performance problem?
Refer to the exhibit.
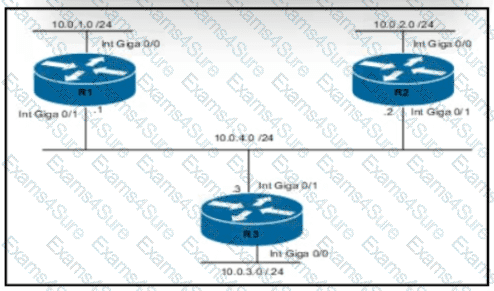
Routers R1 and R3 have the default configuration The router R2 priority is set to 99 Which commands on R3 configure it as the DR in the 10.0 4.0/24 network?
Which interface is used to send traffic to the destination network?
O 10.18.75.113/27 [110/6906] via GO/6
O 10.18.75.113/27 [110/23018] via GO/3
R 10.18.75.113/27 [120/16] via GO/16
R 10.18.75.113/27 [120/14] via GO/23
An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
A network security team noticed that an increasing number of employees are becoming victims of phishing attacks. Which security program should be implemented to mitigate the problem?
Which header must be included in a REST request from an application that requires JSON-formatted content?

Refer to the exhibit. The routers R1-LAB and R2-LAB are configured with link-local addresses. What command must be applied to interface Gi0/0 on R1-LAB for an automated address self-assignment on the IPv6 network?
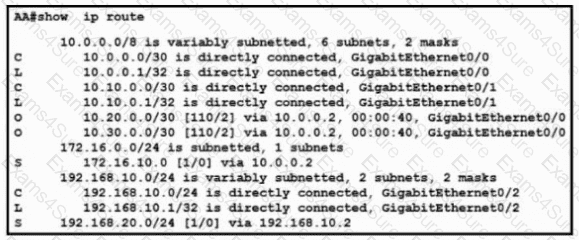
Refer to the exhibit. What is the administrative distance for the advertised prefix that includes the host IP address 10.30.0.1?
Which IP address is used when an administrator must open a web-based management session with a lightweight AP?
What is the function of "off-the-shell" switches in a controller-based network?
Refer to the exhibit.
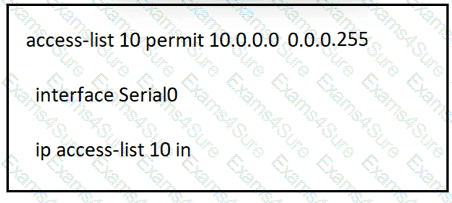
A network administrator must permit traffic from the 10.10.0.0/24 subnet to the WAN on interlace Seria10. What is the effect of the configuration as the administrator applies the command?
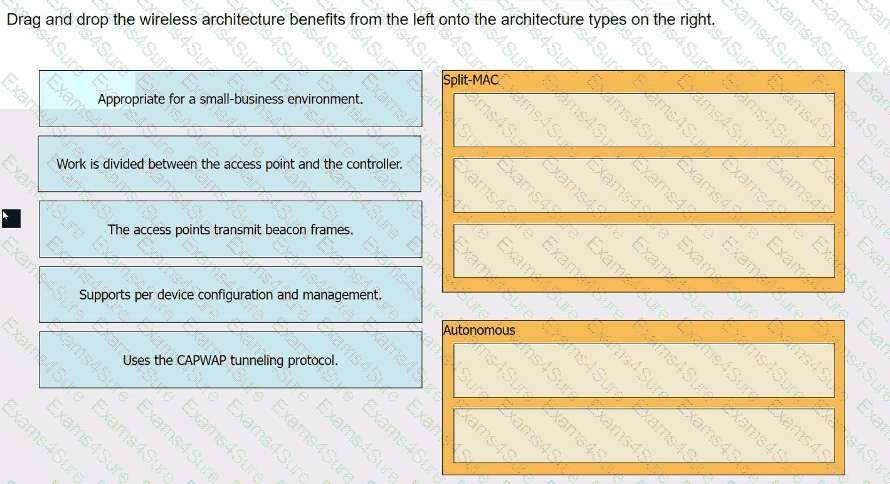
Drag and drop the wireless architecture benefits from the left onto the architecture types on the right.
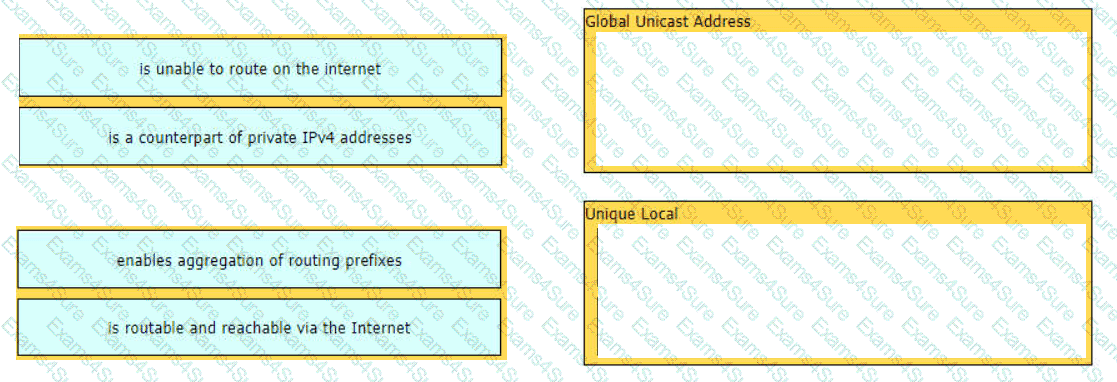
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
A switch is a forwarding a frame out of an interfaces except the interface that received the frame. What is the technical term for this process?
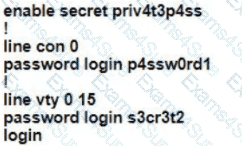
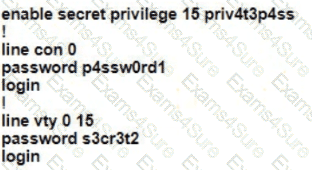
A Cisco engineer is configuring a factory-default router with these three passwords:
• The user EXEC password for console access is p4ssw0rd1
• The user EXEC password for Telnet access is s3cr3t2
• The password for privileged EXEC mode is pnv4t3p4ss Which command sequence must the engineer configured
A)
B)
C)
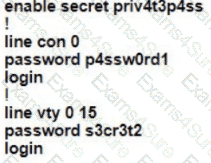
D)

Refer to the exhibit.
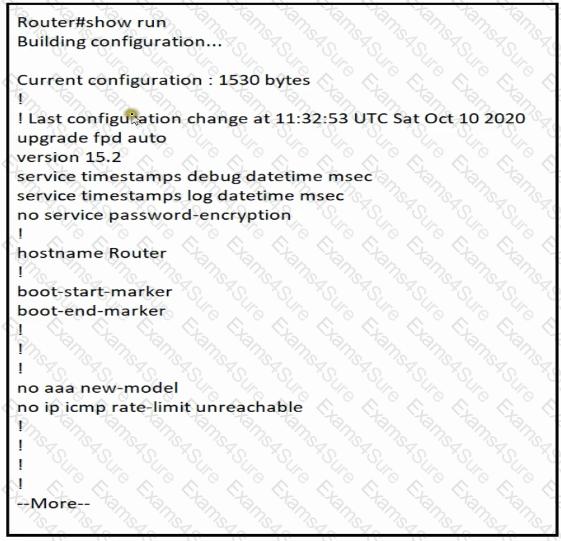
Which minimum configuration items are needed to enable Secure Shell version 2 access to R15?
A)

B)

C)

D)

Refer to the exhibit.

A network engineer must update the configuration on Switch2 so that it sends LLDP packets every minute and the information sent via LLDP is refreshed every 3 minutes Which configuration must the engineer apply?
A)

B)
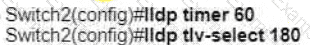
C)

D)
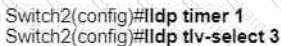

Refer to the exhibit. Which next hop is used to route packets to the application server at 152.168.32.85?
Which combination of methods satisfies the minimum security requirements when a new multifactor authentication solution is deployed?
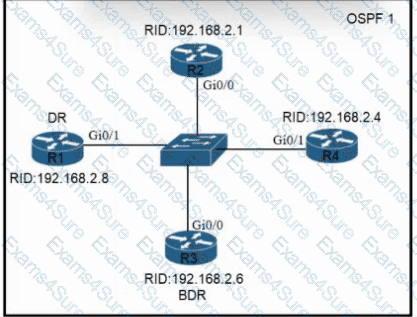
Refer to the exhibit. All routers In the network are configured. R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configured on R2 to be elected as the DR in the network?

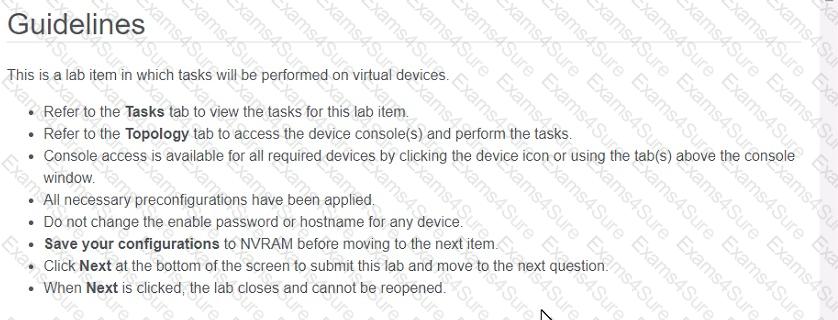
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.
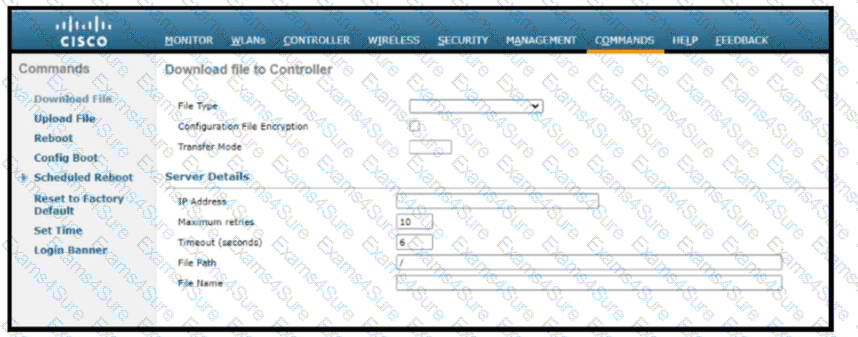
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
Why would a network administrator choose to implement RFC 1918 address space?
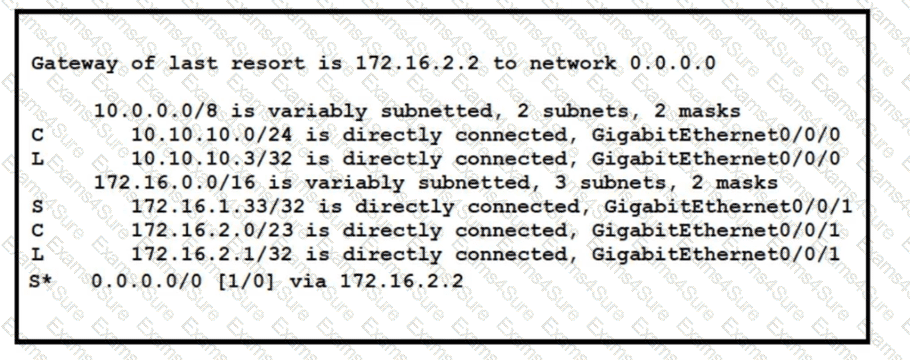
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?
Refer to the exhibit.
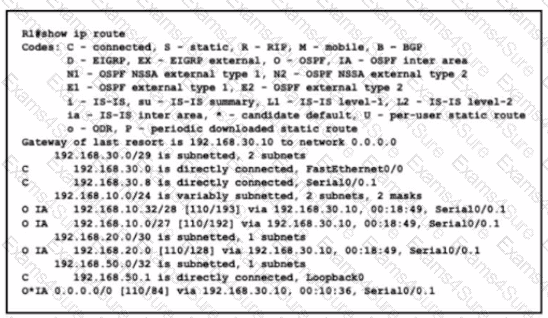
What is the metric for the route to the 192.168.10.33 host?
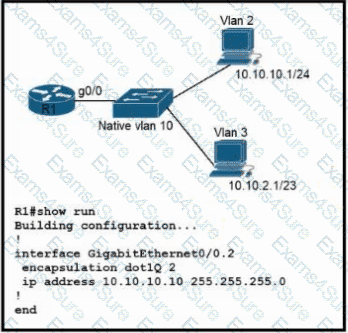
Refer to the exhibit. Configurations for the switch and PCs are complete.
Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?
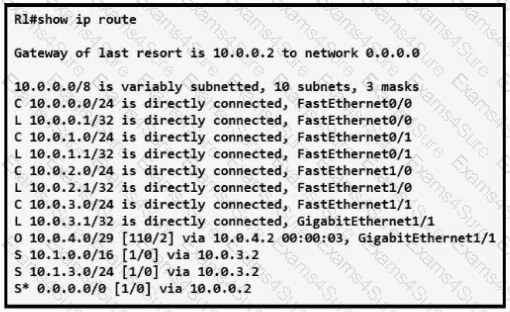
Refer to the exhibit.
How does router R1 forward packets destined to 10.0.4.10?
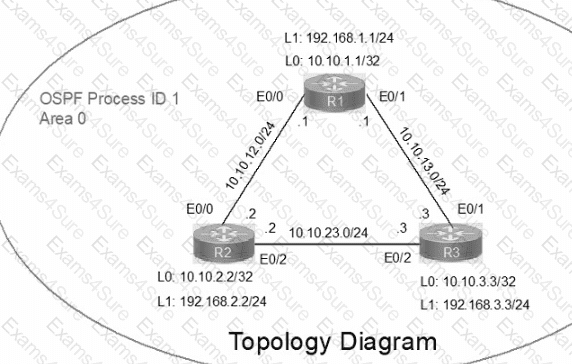
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
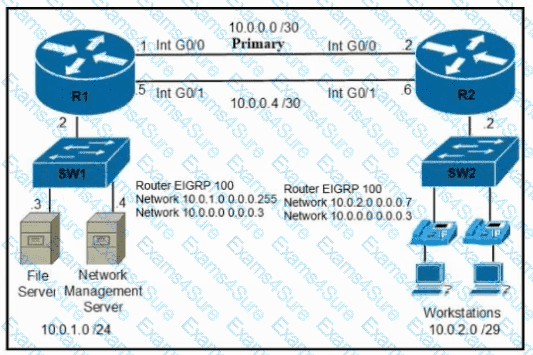
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?
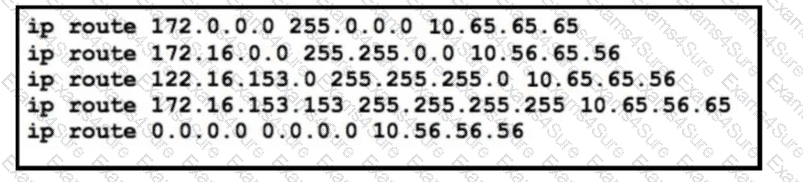
Refer to the exhibit. The static routes were implemented on the border router. What is the next hop IP address for a ping sent to 172.16.153.154 from the border router?
Which interface is used to send traffic to the destination network?
10.249.210.56/25 [90/6144] via G0/15
10.249.210.56/25 [90/45053] via G0/13
10.249.210.56/25 [110/3693] via G0/16
10.249.210.56/25 [110/360] via G0/12
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.



TESTED 02 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.