Certified Kubernetes Security Specialist (CKS)
Last Update 4 days ago
Total Questions : 64
Dive into our fully updated and stable CKS practice test platform, featuring all the latest Kubernetes Security Specialist exam questions added this week. Our preparation tool is more than just a Linux Foundation study aid; it's a strategic advantage.
Our free Kubernetes Security Specialist practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about CKS. Use this test to pinpoint which areas you need to focus your study on.
Cluster: qa-cluster
Master node: master Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context qa-cluster
Task:
Create a NetworkPolicy named restricted-policy to restrict access to Pod product running in namespace dev.
Only allow the following Pods to connect to Pod products-service:
1. Pods in the namespace qa
2. Pods with label environment: stage, in any namespace
Documentation Upgrading kubeadm clusters
You must connect to the correct host . Failure to do so may result in a zero score.
[candidate@base] $ ssh cks000034
Context
The kubeadm provisioned cluster was recently upgraded, leaving one node on a slightly older version due to workload compatibility concerns.
Task
Upgrade the cluster node compute-0 to match the version of the control plane node.
Use a command like the following to connect to the compute node:
[candidate@cks000034] $ ssh compute-0
Do not modify any running workloads in the cluster.
Do not forget to exit from the compute node once you have completed your tasks:
[candidate@icompute-e] $ exit
Documentation Deployments, Pods, Falco
You must connect to the correct host . Failure to do so may result in a zero score.
[candidate@base] $ ssh cks000026
Context
A Pod is misbehaving and poses a security threat to the system.
Task
One of the Pods belonging to the application ollama is misbehaving. It is directly accessing the system's memory reading from the sensitive file /dev/mem.
First, identify the misbehaving Pod accessing /dev/mem.
The cluster uses the Docker Engine as its container runtime . If needed, use the docker command to troubleshoot running containers.
Next, identify the Deployment managing the misbehaving Pod and scale it to zero replicas.
Do not modify the Deployment except for scaling it down.
Do not modify any other Deployments .
Do not delete any Deployments.
Enable audit logs in the cluster, To Do so, enable the log backend, and ensure that
1. logs are stored at /var/log/kubernetes/kubernetes-logs.txt.
2. Log files are retained for 5 days.
3. at maximum, a number of 10 old audit logs files are retained.
Edit and extend the basic policy to log:
1. Cronjobs changes at RequestResponse
2. Log the request body of deployments changes in the namespace kube-system.
3. Log all other resources in core and extensions at the Request level.
4. Don't log watch requests by the "system:kube-proxy" on endpoints or
Context:
Cluster: gvisor
Master node: master1
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context gvisor
Context: This cluster has been prepared to support runtime handler, runsc as well as traditional one.
Task:
Create a RuntimeClass named not-trusted using the prepared runtime handler names runsc.
Update all Pods in the namespace server to run on newruntime.
Documentation Ingress, Service, NGINX Ingress Controller
You must connect to the correct host . Failure to do so may result in a zero score.
[candidate@base] $ ssh cks000032
Context
You must expose a web application using HTTPS routes.
Task
Create an Ingress resource named web in the prod namespace and configure it as follows:
. Route traffic for host web.k8s.local and all paths to the existing Service web
. Enable TLS termination using the existing Secret web-cert.
. Redirect HTTP requests to HTTPS .
You can test your Ingress configuration with the following command:
[candidate@cks000032]$ curl -L http://web.k8s.local
You must connect to the correct host . Failure to do so may
result in a zero score.
[candidato@base] $ ssh cks000023
Task
Analyze and edit the Dockerfile located at /home/candidate/subtle-bee/build/Dockerfile, fixing one instruction present in the file that is a prominent security/best-practice issue.
Do not add or remove instructions; only modify the one existing instruction with a security/best-practice concern.
Do not build the Dockerfile, Failure to do so may result in running out of storage and a zero score.
Analyze and edit the given manifest file /home/candidate/subtle-bee/deployment.yaml, fixing one fields present in the file that are a prominent security/best-practice issue.
Do not add or remove fields; only modify the one existing field with a security/best-practice concern.
Should you need an unprivileged user for any of the tasks, use user nobody with user ID 65535.
Create a Pod name Nginx-pod inside the namespace testing, Create a service for the Nginx-pod named nginx-svc, using the ingress of your choice, run the ingress on tls, secure port.
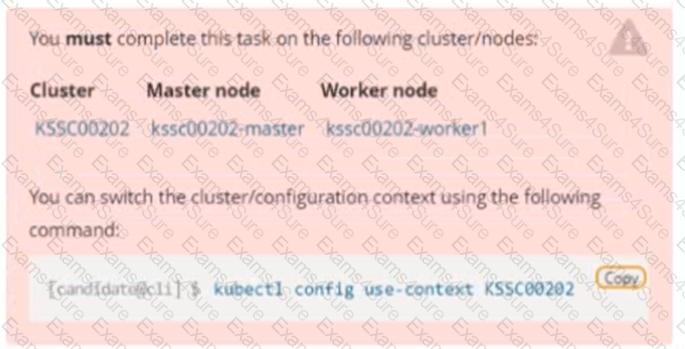
Context
A container image scanner is set up on the cluster, but it's not yet fully integrated into the cluster s configuration. When complete, the container image scanner shall scan for and reject the use of vulnerable images.
Task

Given an incomplete configuration in directory /etc/kubernetes/epconfig and a functional container image scanner with HTTPS endpoint https://wakanda.local:8081 /image_policy :
1. Enable the necessary plugins to create an image policy
2. Validate the control configuration and change it to an implicit deny
3. Edit the configuration to point to the provided HTTPS endpoint correctly
Finally, test if the configuration is working by trying to deploy the vulnerable resource /root/KSSC00202/vulnerable-resource.yml.

Service is running on port 389 inside the system, find the process-id of the process, and stores the names of all the open-files inside the /candidate/KH77539/files.txt, and also delete the binary.


TESTED 28 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.