Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD
Last Update 1 day ago
Total Questions : 60
Dive into our fully updated and stable 300-220 practice test platform, featuring all the latest Cisco Certified Specialist - Threat Hunting and Defending exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our Cisco Certified Specialist - Threat Hunting and Defending practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 300-220. Use this test to pinpoint which areas you need to focus your study on.
Refer to the exhibit.
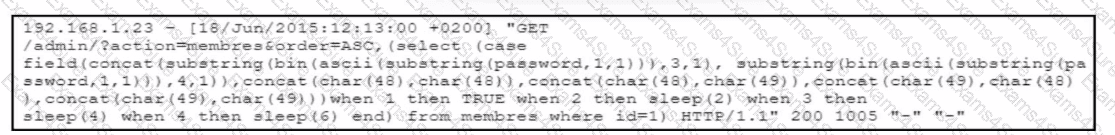
The cybersecurity team at a company detects an ongoing attack directed at the web server that hosts the company website. The team analyzes the logs of the web application firewall and discovers several HTTP requests encoded in Base64. The team decodes the payloads and retrieves the HTTP requests. What did the attackers use to exploit the server?
A structured threat hunt using Cisco Secure Network Analytics confirms abnormal internal SMB traffic consistent with lateral movement. Which action should occur NEXT to improve organizational security posture?
A SOC team wants to detect lateral movement performed using legitimate administrative tools rather than malware. Which telemetry source provides the MOST reliable visibility for this hunting objective?
While analyzing telemetry from Cisco Secure Endpoint and Secure Network Analytics, analysts observe that an adversary consistently avoids deploying malware and instead abuses built-in administrative tools. Why does this observation matter for attribution?
Refer to the exhibit.
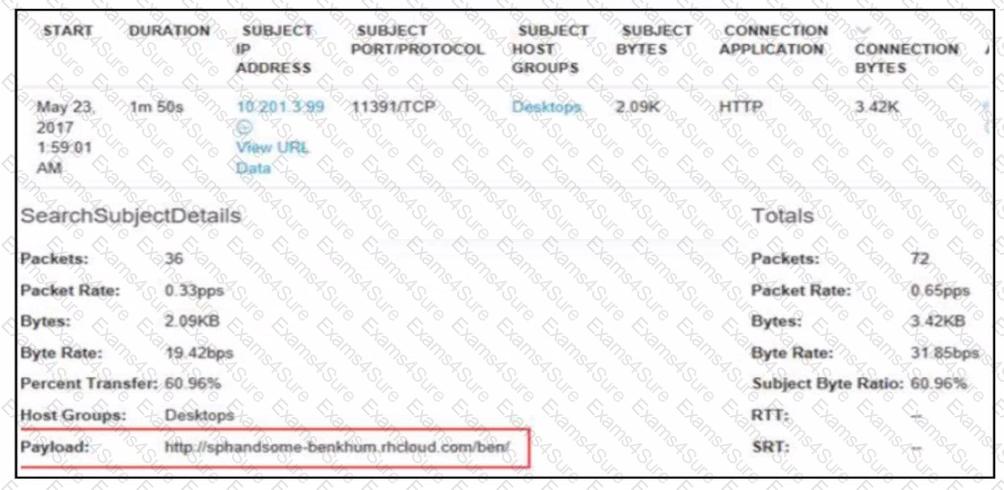
A security analyst receives an alert from Cisco Secure Network Analytics (formerly StealthWatch) with the C2 category. Which information aids the investigation?
A threat hunter usesCisco Secure Network Analytics (Stealthwatch)to identify potential command-and-control traffic. Which characteristic MOST strongly indicates beaconing behavior?
Refer to the exhibit.
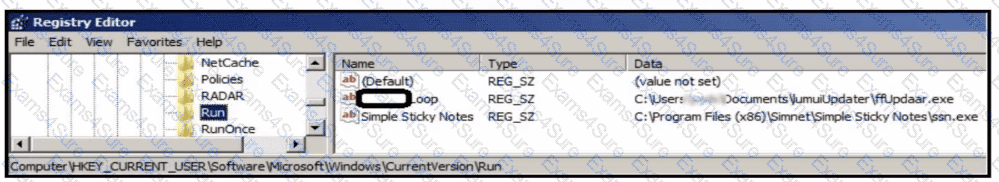
An analyst is evaluating artifacts and logs collected from recent breach. In the logs, ATP established persistency of malware by placing a path to the executable in a specific registry entry. What is the difference between the ATP's approach and using HKEY LOCAL MACHINE\Software\Microsoft\Windows\CurrentVersion\Run instead?
A SOC manager wants to evaluate whether the organization’s Cisco-based threat hunting program is improving over time. Which metric BEST reflects increased threat hunting effectiveness?
A security team is performing threat modeling for a hybrid environment consisting of on-prem Active Directory and Azure A
D.
The team wants to identify how an attacker could move from a compromised cloud identity to full on-prem domain dominance. Which modeling focus is MOST appropriate?Refer to the exhibit.
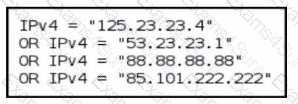
A threat-hunting team makes an EDR query to detect possible C2 outbound communication across all endpoints. Which level of the Pyramid of Pain is being used?


TESTED 05 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.