Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator
Last Update 4 days ago
Total Questions : 65
Dive into our fully updated and stable FCSS_EFW_AD-7.6 practice test platform, featuring all the latest Fortinet Certified Professional Network Security exam questions added this week. Our preparation tool is more than just a Fortinet study aid; it's a strategic advantage.
Our free Fortinet Certified Professional Network Security practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about FCSS_EFW_AD-7.6. Use this test to pinpoint which areas you need to focus your study on.
Refer to the exhibits.
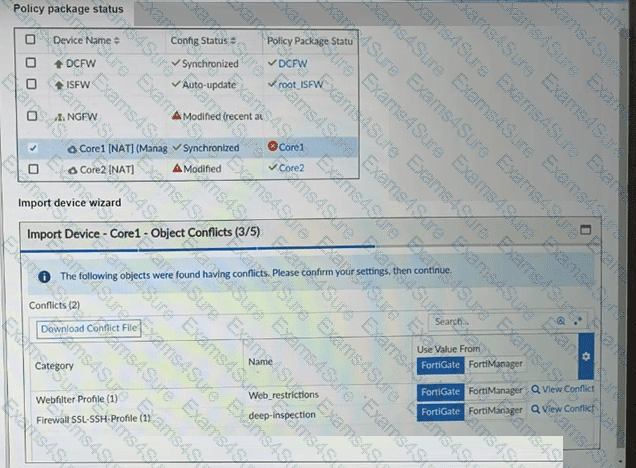
A policy package conflict status and information from the import device wizard in the Core1 VDOM are shown. When you import a policy package, the following message appears for the Web_restrictions web filter profile and the deep-inspection SSL-SSH profile: "The following objects were found having conflicts. Please confirm your settings, then continue." The Web_restrictions and deep-inspection profiles are used by other FortiGate devices within FortiManager. Which step must you take to resolve the issue? (Choose one answer)
Refer to the exhibits. The exhibits show a network topology, a firewall policy, and an SSL/SSH inspection profile configuration.
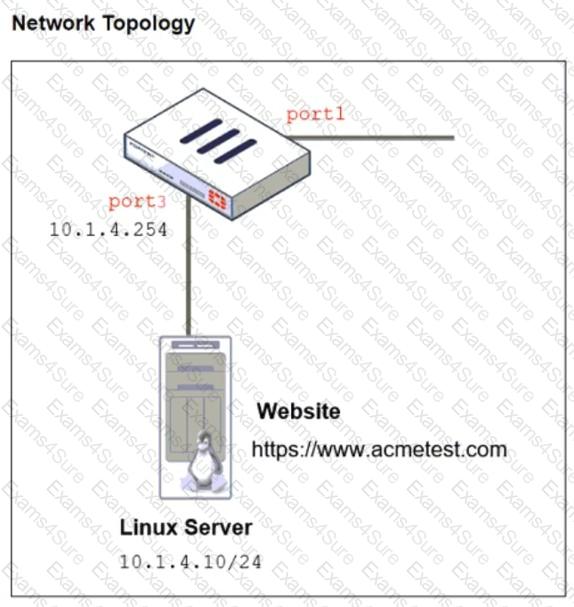
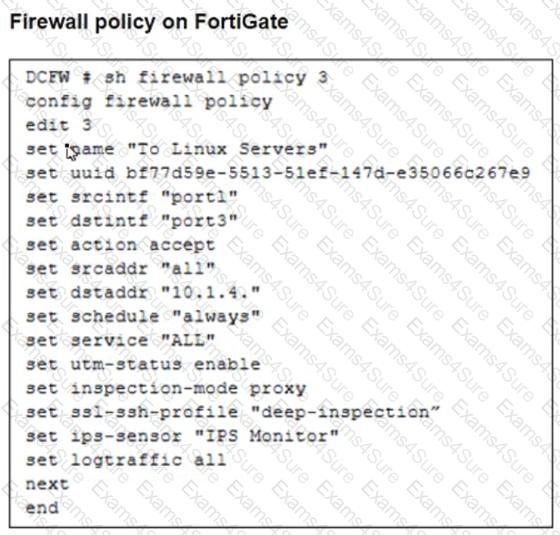
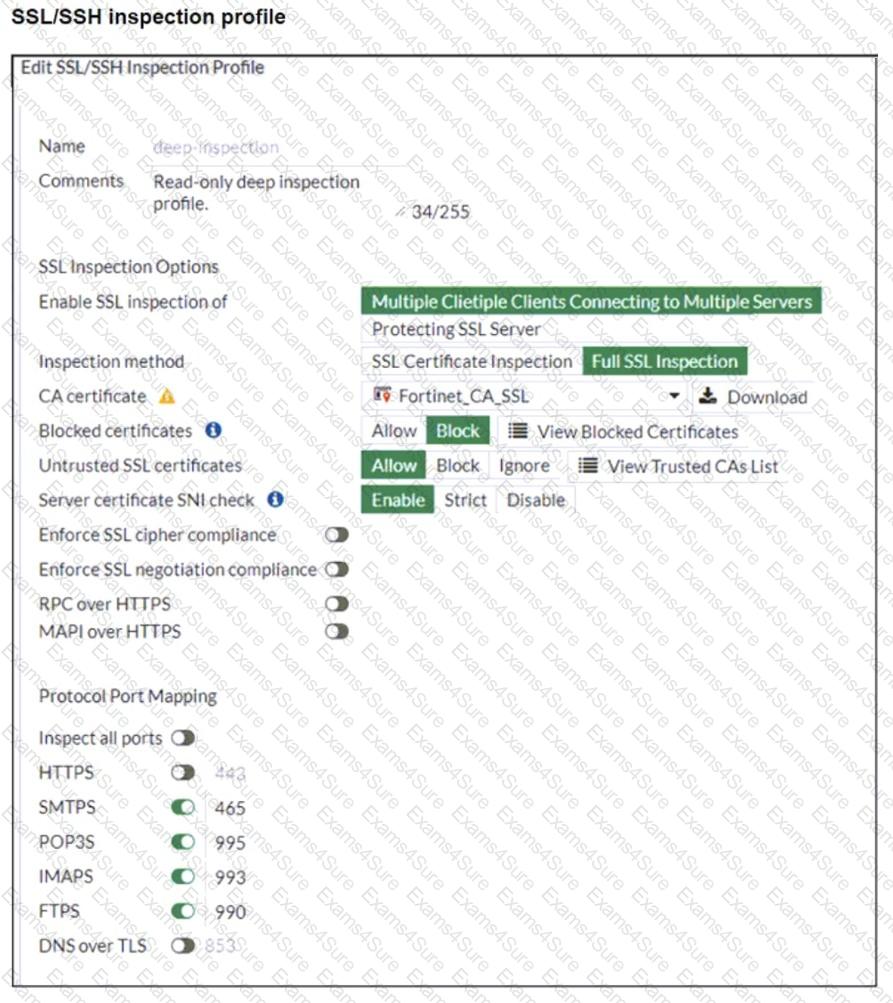
Why is FortiGate unable to detect HTTPS attacks on firewall policy ID 3 targeting the Linux server?
What is the initial step performed by FortiGate when handling the first packets of a session?
An administrator configured the FortiGate devices in an enterprise network to join the Fortinet Security Fabric. The administrator has a list of IP addresses that must be blocked by the data center firewall. This list is updated daily.
How can the administrator automate a firewall policy with the daily updated list?
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Which two statements about IKEv2 are true if an administrator decides to implement IKEv2 in the VPN topology? (Choose two.)
Refer to the exhibit, which shows a network diagram showing the addition of site 2 with an overlapping network segment to the existing VPN IPsec connection between the hub and site 1.
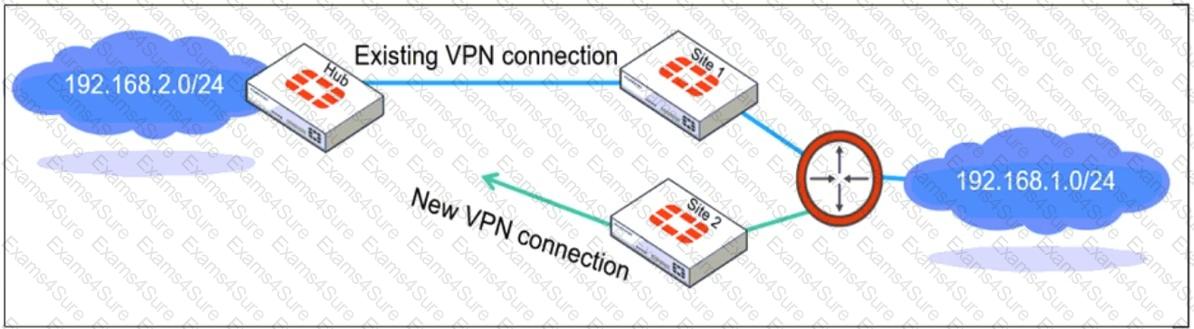
Which IPsec phase 2 configuration must an administrator make on the FortiGate hub to enable equal-cost multi-path (ECMP) routing when multiple remote sites connect with overlapping subnets?
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
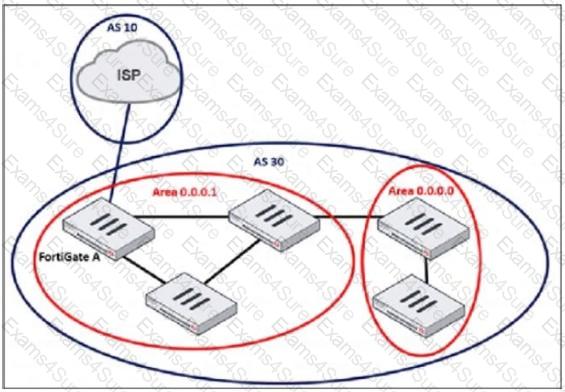
The administrator must configure the BGP section of FortiGate A to give internet access to the enterprise network.
Which command must the administrator use to establish a connection with the internet service provider?
Refer to the exhibit, which shows a revision history window in the FortiManager device layer.
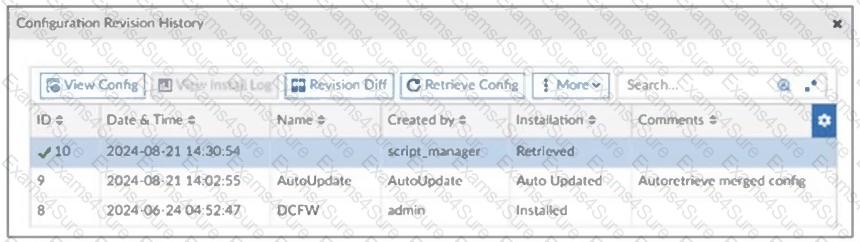
The IT team is trying to identify the administrator responsible for the most recent update in the FortiGate device database.
Which conclusion can you draw about this scenario?
Refer to the exhibit, which shows an OSPF network.
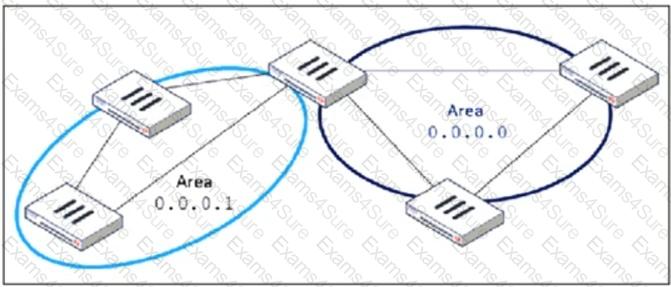
Which configuration must the administrator apply to optimize the OSPF database?


TESTED 14 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.