CompTIA Cloud+ (2025)
Last Update 4 days ago
Total Questions : 256
Dive into our fully updated and stable CV0-004 practice test platform, featuring all the latest CompTIA Cloud+ exam questions added this week. Our preparation tool is more than just a CompTIA study aid; it's a strategic advantage.
Our CompTIA Cloud+ practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about CV0-004. Use this test to pinpoint which areas you need to focus your study on.
The company's IDS has reported an anomaly. The cloud engineer remotely accesses the cloud instance, runs a command, and receives the following information:
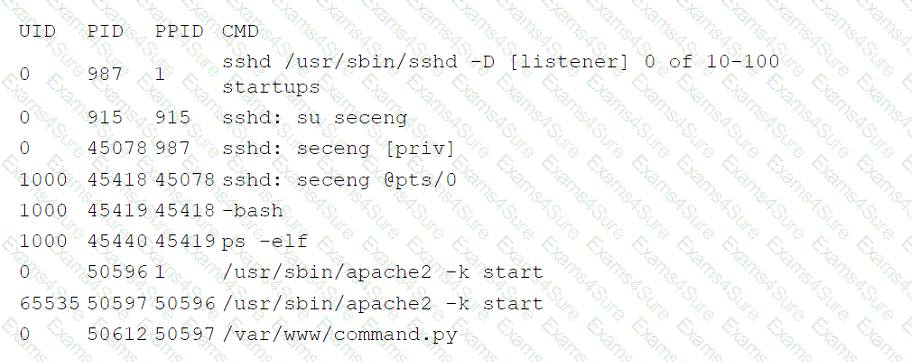
Which of the following is the most likely root cause of this anomaly?
An engineer wants lo scale several cloud workloads on demand. Which of the following approaches is the most suitable?
A systems administrator is provisioning VMs according to the following requirements:
· A VM instance needs to be present in at least two data centers.
. During replication, the application hosted on the VM tolerates a maximum latency of one second.
· When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?
A systems administrator needs to configure backups for the company's on-premises VM cluster. The storage used for backups will be constrained on free space until the company
can implement cloud backups. Which of the following backup types will save the most space, assuming the frequency of backups is kept the same?
Which of the following is used to deliver code quickly and efficiently across the development, test, and production environments?
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
Which of the following would allow a cloud engineer to flatten a deeply nested JSON log to improve readability for analysts?
A security analyst reviews the daily logs and notices the following suspicious activity:
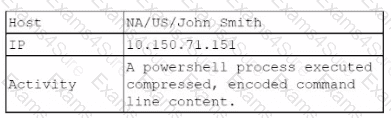
The analyst investigates the firewall logs and identities the following:
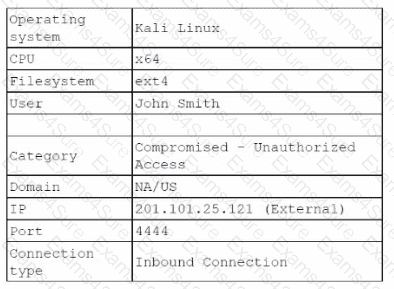
Which of the following steps should the security analyst take next to resolve this issue? (Select two).
A SaaS provider introduced new software functionality for customers as part of quarterly production enhancements. After an update is implemented, users cannot locate certain transactions from an inbound integration. During the investigation, the application owner finds the following error in the logs:
Error: REST API - Deprecated call is no longer supported in this release.
Which of the following is the best action for the application owner to take to resolve the issue?
Which of the following would help a project manager identify that project goals have been reached?


TESTED 04 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.