Fortinet NSE 7 - OT Security 7.2
Last Update 3 days ago
Total Questions : 69
Dive into our fully updated and stable NSE7_OTS-7.2 practice test platform, featuring all the latest NSE 7 Network Security Architect exam questions added this week. Our preparation tool is more than just a Fortinet study aid; it's a strategic advantage.
Our free NSE 7 Network Security Architect practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about NSE7_OTS-7.2. Use this test to pinpoint which areas you need to focus your study on.
Refer to the exhibit.
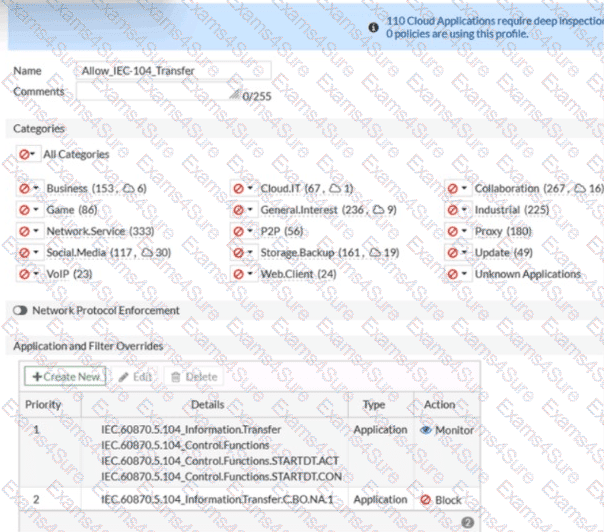
An OT network security audit concluded that the application sensor requires changes to ensure the correct security action is committed against the overrides filters.
Which change must the OT network administrator make?
Refer to the exhibits.
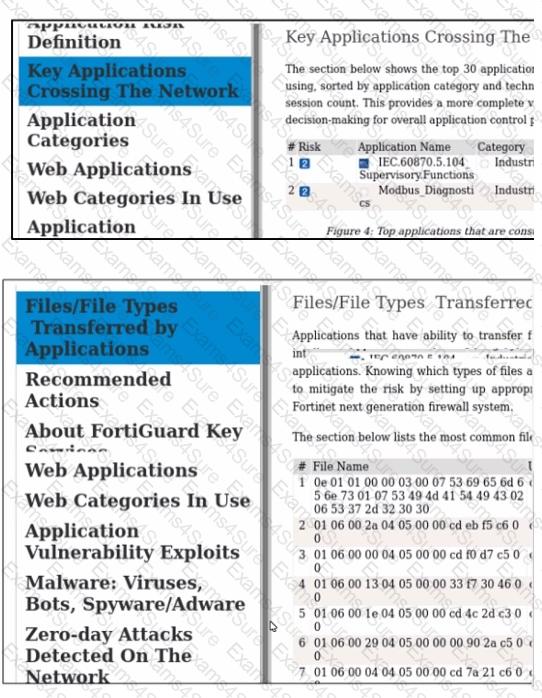
Which statement about some of the generated report elements from FortiAnalyzer is true?
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
Refer to the exhibit.
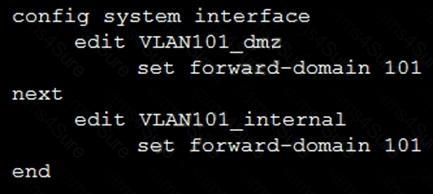
Given the configurations on the FortiGate, which statement is true?
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-party company while continuing to secure the ICS networks?
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
Refer to the exhibit.
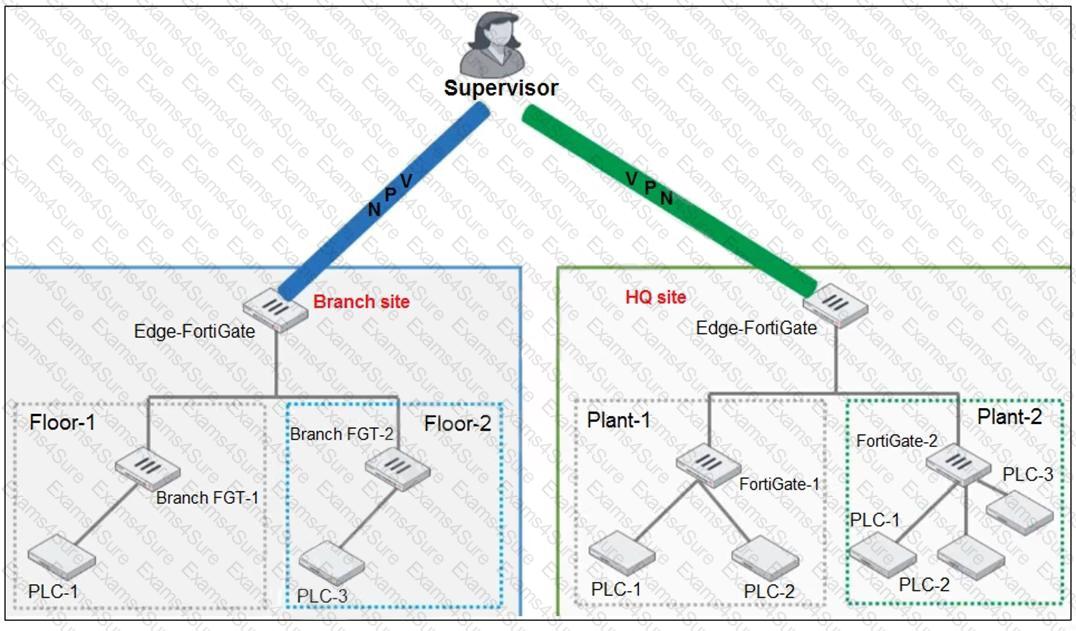
You need to configure VPN user access for supervisors at the breach and HQ sites using the same soft FortiToken. Each site has a FortiGate VPN gateway.
What must you do to achieve this objective?
Refer to the exhibit.
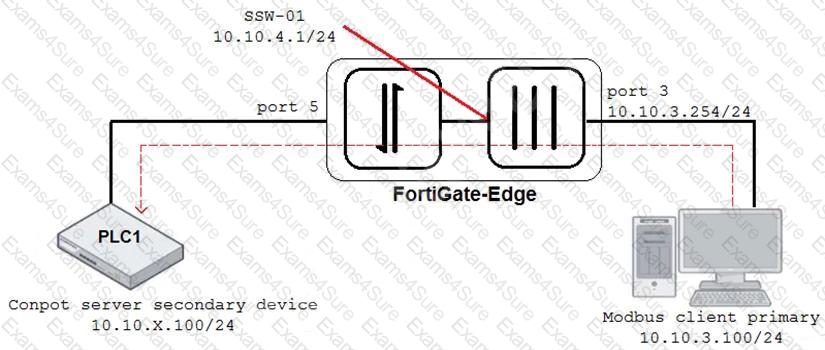
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
Refer to the exhibit.
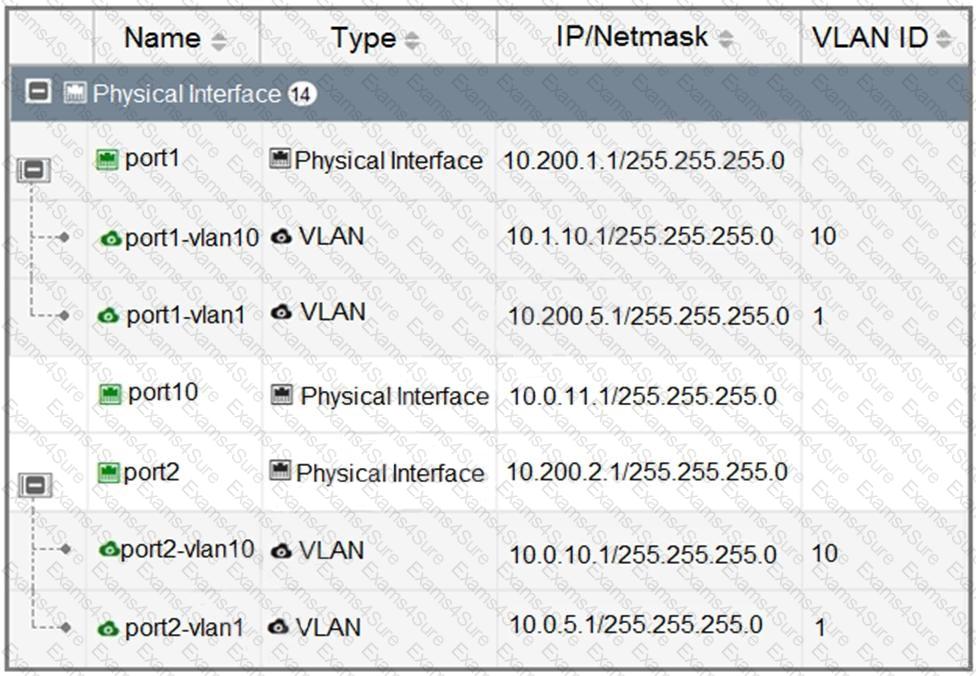
Which statement about the interfaces shown in the exhibit is true?


TESTED 28 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.