Certified SOC Analyst (CSA v2)
Last Update 3 days ago
Total Questions : 200
Dive into our fully updated and stable 312-39 practice test platform, featuring all the latest CSA exam questions added this week. Our preparation tool is more than just a ECCouncil study aid; it's a strategic advantage.
Our free CSA practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 312-39. Use this test to pinpoint which areas you need to focus your study on.
A company's SIEM is generating a high number of alerts, overwhelming the SOC team with false positives and irrelevant notifications. This reduces efficiency as analysts struggle to identify genuine incidents. To address this, the security team refines their approach by defining clear threat detection scenarios aligned with their environment and risk profile. This is expected to improve detection accuracy and streamline incident response. Which process is the team implementing?
John, a threat analyst at GreenTech Solutions, wants to gather information about specific threats against the organization. He started collecting information from various sources, such as humans, social media, chat room, and so on, and created a report that contains malicious activity.
Which of the following types of threat intelligence did he use?
Which of the following attack inundates DHCP servers with fake DHCP requests toexhaust all available IP addresses?
The Syslog message severity levels are labelled from level 0 to level 7.
What does level 0 indicate?
Jannet works in a multinational corporation that operates multiple data centers, cloud environments, and on-premises systems. As a SOC analyst, she notices that security incidents are taking too long to detect and investigate. After analyzing this, she discovers that logs from firewalls, endpoint security solutions, authentication servers, and cloud applications are scattered across different systems in various formats. Her team has to manually convert logs into a readable format before investigating incidents. What approach should she implement to accept logs from heterogeneous sources with different formats, convert them into a common format, and improve incident detection and response time?
A mid-sized financial institution’s SOC is overwhelmed by thousands of daily alerts, many based on Indicators of Compromise (IoCs) such as suspicious IPs, hashes, and domains. These alerts lack context about whether they truly pose a threat. Analysts waste time on low-priority incidents while severe threats may be missed. The team lacks tools and intelligence to correlate IoCs with real-world threats, making prioritization difficult and causing alert fatigue. Which poses the greatest challenge in this environment?
An organization is implementing and deploying the SIEM with following capabilities.
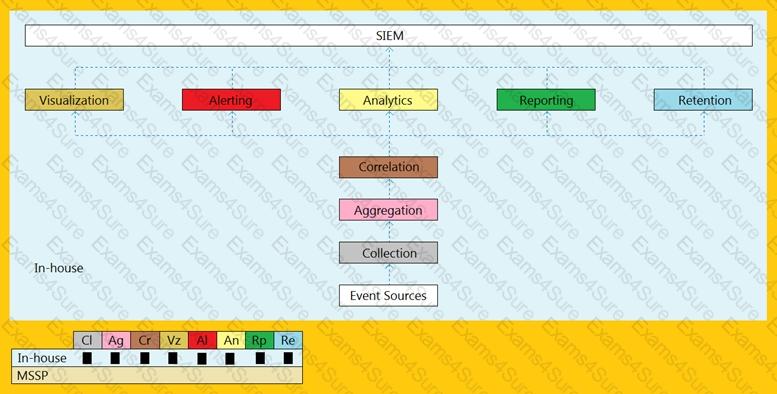
What kind of SIEM deployment architecture the organization is planning to implement?
During routine monitoring, the SIEM detects an unusual spike in outbound data transfer from a critical database server. The typical outbound traffic for this server is around 5 MB/hour, but in the past 10 minutes, it has sent over 500 MB to an external IP address. No predefined signatures match this activity, but the SIEM raises an alert due to deviations from the server’s normal behavior profile. Which detection method is responsible for this alert?
As a SOC Administrator at a mid-sized financial institution, you noticed intermittent network slowdowns and unexplained high memory usage across multiple critical systems. Your initial analysis found no traces of malware, but a forensic investigation revealed unauthorized scheduled tasks that executed during off-peak hours. These tasks ran obfuscated scripts that connected to an external command-and-control (C2) server. Further investigations showed that the adversary had gained access months ago through a compromised VPN account, leveraging stolen credentials from a phishing campaign. Which phase of the Advanced Persistent Threat (APT) lifecycle does this scenario align with?


TESTED 27 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.