Netskope Certified Cloud Security Architect Exam
Last Update 3 days ago
Total Questions : 68
Dive into our fully updated and stable NSK300 practice test platform, featuring all the latest NCCSA exam questions added this week. Our preparation tool is more than just a Netskope study aid; it's a strategic advantage.
Our free NCCSA practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about NSK300. Use this test to pinpoint which areas you need to focus your study on.
You have deployed Netskope to all users of the organization and you are now ready to begin ingesting all events, alerts, and Web transactions into your SIEM as a part of your requirements.
What are three ways in which you would accomplish this task? (Choose three.)
Users in your network are attempting to reach a website that has a self-signed certificate using a GRE tunnel to Netskope. They are currently being blocked by Netskope with an SSL error. How would you allow this traffic?
You have multiple networking clients running on an endpoint and client connectivity is a concern. You are configuring co-existence with a VPN solution in this scenario, what is recommended to prevent potential routing issues?
You have an NG-SWG customer that currently steers all Web traffic to Netskope using the Netskope Client. They have identified one new native application on Windows devices that is a certificate-pinned application. Users are not able to access the application due to certificate pinning. The customer wants to configure the Netskope Client so that the traffic from the application is steered to Netskope and the application works as expected.
Which two methods would satisfy the requirements? (Choose two.)
Review the exhibit.
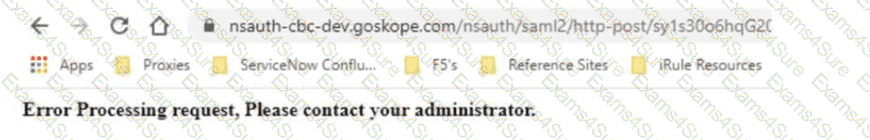
Netskope has been deployed using Cloud Explicit Proxy and PAC files. Authentication using Active Directory Federation Services (ADFS) has been configured for SAML Forward Proxy auth. When the users open their browser and try to go to a site, they receive the error shown in the exhibit.
What is a reason for this error?
You are attempting to merge two Advanced Analytics reports with DLP incidents: Report A with 3000 rows and Report B with 6000 rows. Once merged, you notice that the merged report is missing a significant number of rows.
What is causing this behavior?
A hospital has a patient form that they share with their patients over Gmail. The blank form can be freely shared among anyone. However, if the form has any information filled out. the document is considered confidential.
Which rule type should be used in the DLP profile to match such a document?
You are implementing Netskope Cloud Exchange in your company lo include functionality provided by third-party partners. What would be a reason for using Netskope Cloud Risk Exchange in this scenario?
You are architecting a Netskope steering configuration for devices that are not owned by the organization The users could be either on-premises or off-premises and the architecture requires that traffic destined to the company's instance of Microsoft 365 be steered to Netskope for inspection.
How would you achieve this scenario from a steering perspective?
You want to verify that Google Drive is being tunneled to Netskope by looking in the nsdebuglog file. You are using Chrome and the Netskope Client to steer traffic. In this scenario, what would you expect to see in the log file?
A)

B)
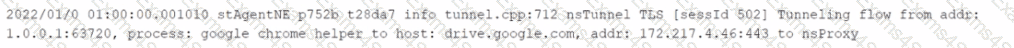
C)
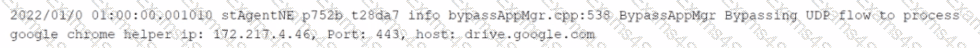
D)



TESTED 28 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.