Fortinet NSE 7 - Security Operations 7.6 Architect
Last Update 1 day ago
Total Questions : 57
Dive into our fully updated and stable NSE7_SOC_AR-7.6 practice test platform, featuring all the latest Fortinet Certified Professional Security Operations exam questions added this week. Our preparation tool is more than just a Fortinet study aid; it's a strategic advantage.
Our free Fortinet Certified Professional Security Operations practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about NSE7_SOC_AR-7.6. Use this test to pinpoint which areas you need to focus your study on.
Refer to the exhibits.
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?
Refer to the exhibit.
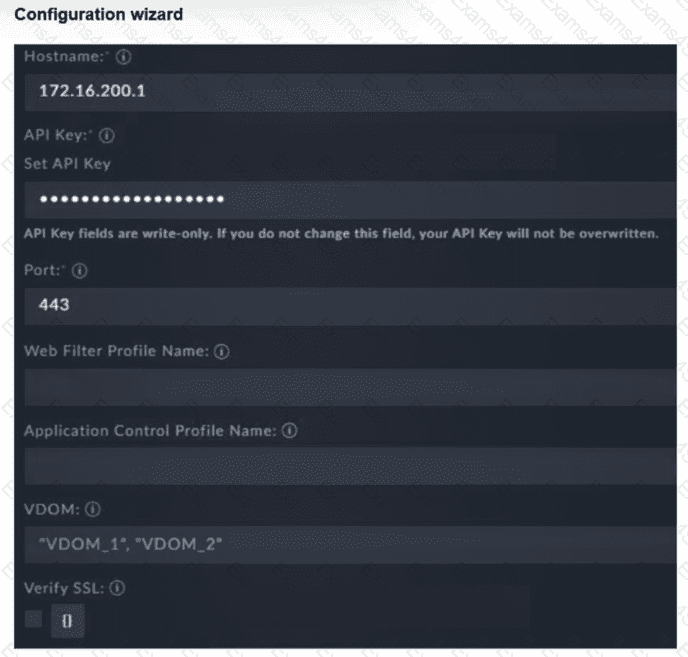
You must configure the FortiGate connector to allow FortiSOAR to perform actions on a firewall. However, the connection fails. Which two configurations are required? (Choose two answers)
Which of the following are critical when analyzing and managing events and incidents in a SOC? (Choose two answers)
Which two ways can you create an incident on FortiAnalyzer? (Choose two answers)
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
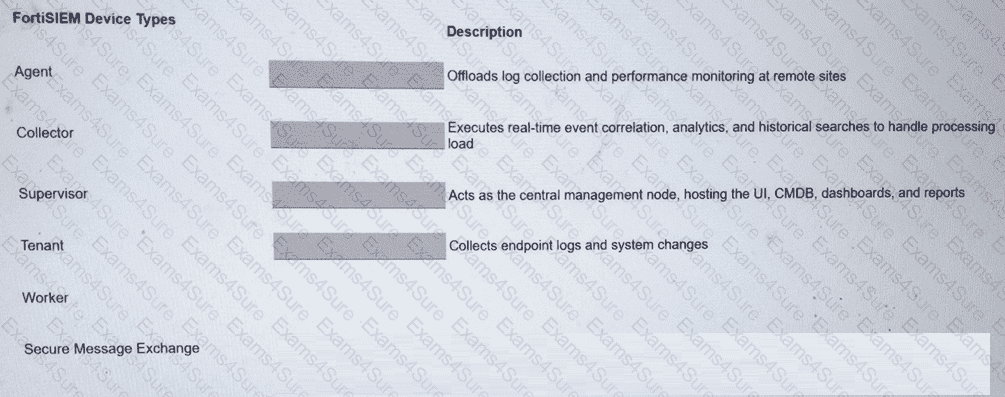
Match the FortiSIEM device type to its description. Select each FortiSIEM device type in the left column, hold and drag it to the blank space next to its corresponding description in the column on the right.
Which three factors does the FortiSIEM rules engine use to determine the count when it evaluates the aggregate condition COUNT (Matched Events) on a specific subpattern? (Choose three answers)
Refer to the exhibit.
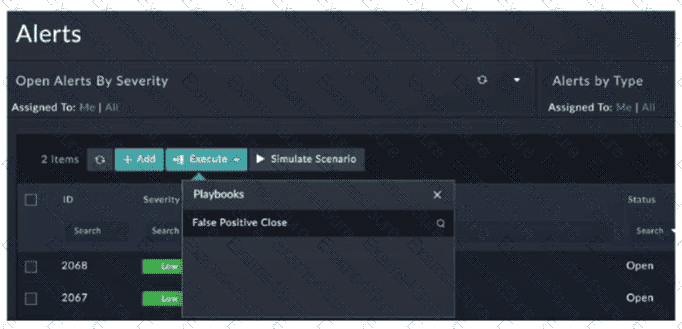
You configured a playbook namedFalse Positive Close, and want to run it to verify if it works. However, when you clickExecuteand search for the playbook, you do not see it listed. Which two reasons could be the cause of the problem? (Choose two answers)


TESTED 21 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.