CompTIA SecurityX Certification Exam
Last Update 3 days ago
Total Questions : 326
Dive into our fully updated and stable CAS-005 practice test platform, featuring all the latest CompTIA CASP exam questions added this week. Our preparation tool is more than just a CompTIA study aid; it's a strategic advantage.
Our free CompTIA CASP practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about CAS-005. Use this test to pinpoint which areas you need to focus your study on.
An organization is increasing its focus on training that addresses new social engineering and phishing attacks. Which of the following is the organization most concerned about?
A company discovers intellectual property data on commonly known collaboration web applications that allow the use of slide templates. The systems administrator is reviewing the configurations of each tool to determine how to prevent this issue. The following security solutions are deployed:
CASB
SASE
WAF
EDR
Firewall
IDS
SIEM
DLP endpoints
Which of the following should the administrator do to address the issue?
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
A company undergoing digital transformation is reviewing the resiliency of a CSP and is concerned about meeting SLA requirements in the event of a CSP incident. Which of the following would be best to proceed with the transformation?
A nation-state actor is exposed for attacking large corporations by establishing persistence in smaller companies that are likely to be acquired by these large corporations. The actor then provisions user accounts in the companies for use post-acquisition. Before an upcoming acquisition, a security officer conducts threat modeling with this attack vector. Which of the following practices is the best way to investigate this threat?
While reviewing recent modem reports, a security officer discovers that several employees were contacted by the same individual who impersonated a recruiter. Which of the following best describes this type of correlation?
After a vendor identified a recent vulnerability, a severity score was assigned to the vulnerability. A notification was also publicly distributed. Which of the following would most likely include information regarding the vulnerability and the recommended remediation steps?
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
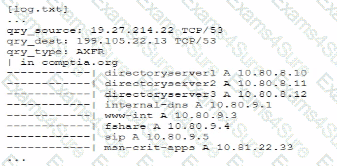
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A security administrator needs to review the efficacy of the detection rules configured on the SIEM by employing real-world attacker TTPs. Which of the following actions should the security administrator take to accomplish this objective?
A Chief Information Security Officer requests an action plan to remediate vulnerabilities. A security analyst reviews the output from a recent vulnerability scan and notices hundreds of unique vulnerabilities. The output includes the CVSS score, IP address, hostname, and the list of vulnerabilities. The analyst determines more information is needed in order to decide which vulnerabilities should be fixed immediately. Which of the following is the best source for this information?


TESTED 05 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.