Securing Networks with Cisco Firepower (300-710 SNCF)
Last Update 3 days ago
Total Questions : 278
Securing Networks with Cisco Firepower (300-710 SNCF) is stable now with all latest exam questions are added 3 days ago. Incorporating 300-710 practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the Securing Networks with Cisco Firepower (300-710 SNCF) exam format, identifying knowledge gaps, applying theoretical knowledge in Cisco practical scenarios, you are setting yourself up for success. 300-710 exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
300-710 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through 300-710 dumps allows you to practice pacing yourself, ensuring that you can complete all Securing Networks with Cisco Firepower (300-710 SNCF) exam questions within the allotted time frame without sacrificing accuracy.
Which protocol establishes network redundancy in a switched Firepower device deployment?
An administrator is optimizing the Cisco FTD rules to improve network performance, and wants to bypass inspection for certain traffic types to reduce the load on the Cisco FT
D.
Which policy must be configured to accomplish this goal?With Cisco Firepower Threat Defense software, which interface mode must be configured to passively receive traffic that passes through the appliance?
An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements?
When deploying a Cisco ASA Firepower module, an organization wants to evaluate the contents of the traffic without affecting the network. It is currently configured to have more than one instance of the same device on the physical appliance Which deployment mode meets the needs of the organization?
An organization does not want to use the default Cisco Firepower block page when blocking HTTP traffic. The organization wants to include information about its policies and procedures to help educate the users whenever a block occurs. Which two steps must be taken to meet these requirements? (Choose two.)
An engineer is configuring Cisco FMC and wants to allow multiple physical interfaces to be part of the same VLAN. The managed devices must be able to perform Layer 2 switching between interfaces, including sub-interfaces. What must be configured to meet these requirements?
In which two ways do access control policies operate on a Cisco Firepower system? (Choose two.)
Which Firepower feature allows users to configure bridges in routed mode and enables devices to perform Layer 2 switching between interfaces?
An engineer configures a network discovery policy on Cisco FM
C.
Upon configuration, it is noticed that excessive and misleading events filing the database and overloading the Cisco FMC.
A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configuration change must be made to alleviate this issue?A network administrator notices that remote access VPN users are not reachable from inside the network. It is determined that routing is configured correctly, however return traffic is entering the firewall but not leaving it What is the reason for this issue?
What is the disadvantage of setting up a site-to-site VPN in a clustered-units environment?
Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain environment?
Which group within Cisco does the Threat Response team use for threat analysis and research?
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
After deploying a network-monitoring tool to manage and monitor networking devices in your organization, you realize that you need to manually upload an MIB for the Cisco FM
C.
In which folder should you upload the MIB file?Which Cisco Firepower feature is used to reduce the number of events received in a period of time?
Which command should be used on the Cisco FTD CLI to capture all the packets that hit an interface?
An organization wants to secure traffic from their branch office to the headquarter building using Cisco Firepower devices, They want to ensure that their Cisco Firepower devices are not wasting resources on inspecting the VPN traffic. What must be done to meet these requirements?
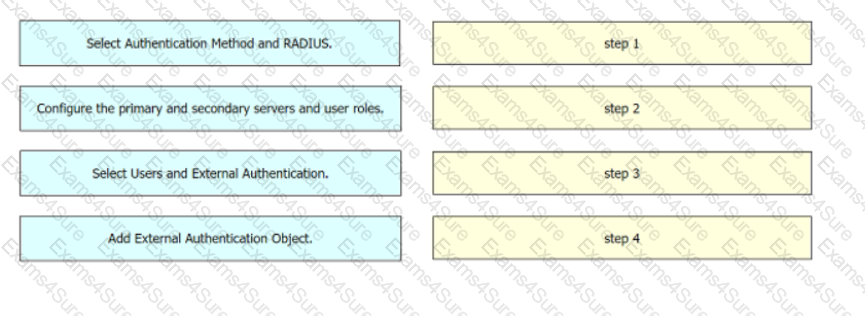
Drag and drop the configuration steps from the left into the sequence on the right to enable external authentication on Cisco FMC to a RADIUS server.
Which feature within the Cisco FMC web interface allows for detecting, analyzing and blocking malware in network traffic?
An organization is setting up two new Cisco FTD devices to replace their current firewalls and cannot have any network downtime During the setup process, the synchronization between the two devices is failing What action is needed to resolve this issue?
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10 10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
Refer to the exhibit.
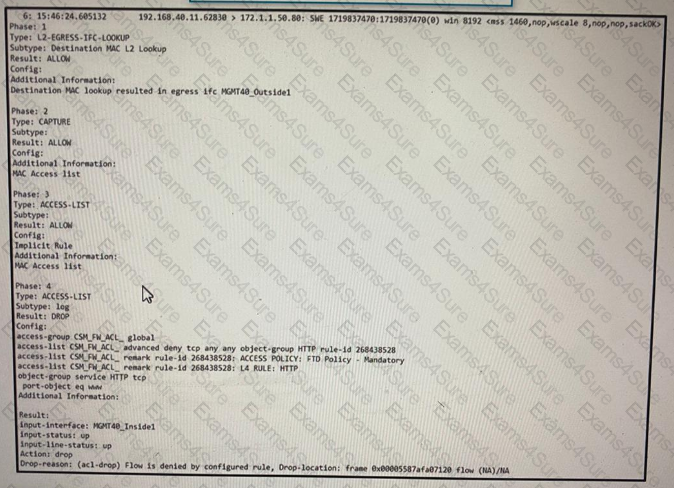
What must be done to fix access to this website while preventing the same communication to all other websites?
The network administrator wants to enhance the network security posture by enabling machine learning tor malware detection due to a concern with suspicious Microsoft executable file types that were seen while creating monthly security reports for the CIO. Which feature must be enabled to accomplish this goal?
A connectivity issue is occurring between a client and a server which are communicating through a Cisco Firepower device While troubleshooting, a network administrator sees that traffic is reaching the server, but the client is not getting a response Which step must be taken to resolve this issue without initiating traffic from the client?
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two.)
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
Which Cisco Advanced Malware Protection for Endpoints policy is used only for monitoring endpoint actively?
What is the maximum SHA level of filtering that Threat Intelligence Director supports?
In a Cisco AMP for Networks deployment, which disposition is returned if the cloud cannot be reached?
Which two features of Cisco AMP for Endpoints allow for an uploaded file to be blocked? (Choose two.)
Which action should you take when Cisco Threat Response notifies you that AMP has identified a file as malware?
Which two conditions are necessary for high availability to function between two Cisco FTD devices? (Choose two.)


TESTED 10 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.