Disaster Recovery Professional Practice Test
Last Update 3 days ago
Total Questions : 290
Disaster Recovery Professional Practice Test is stable now with all latest exam questions are added 3 days ago. Incorporating 312-76 practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the Disaster Recovery Professional Practice Test exam format, identifying knowledge gaps, applying theoretical knowledge in ECCouncil practical scenarios, you are setting yourself up for success. 312-76 exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
312-76 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through 312-76 dumps allows you to practice pacing yourself, ensuring that you can complete all Disaster Recovery Professional Practice Test exam questions within the allotted time frame without sacrificing accuracy.
In which of the following prototyping, a version of the system is built to check the requirements and is then discarded?
Which of the following cryptographic system services ensures that the information will not be disclosed to any unauthorized person on a local network?
Which of the following DRP tests is plan distributed, and reviewed by the business units for its
thoroughness and effectiveness?
You work as a security manager for SoftTech Inc. You along with your team are doing the disaster recovery for your project. Which of the following steps are performed by you for secure recovery based on the extent of the disaster and the organization's recovery ability?
Each correct answer represents a part of the solution. Choose three.
Fill in the blank with the appropriate phrase.
__________________ is the process of obtaining access using legitimate credentials, and then attempting to leverage that into access to unauthorized system resources.
Which of the following plans is documented and organized for emergency response, backup operations, and recovery maintained by an activity as part of its security program that will ensure the availability of critical resources and facilitates the continuity of operations in an emergency situation?
Which of the following actions can be performed by using the principle of separation of duties?
Which of the following statements are true about classless routing protocols?
Each correct answer represents a complete solution. Choose two.
Which of the following processes helps to quantify the impact of potential threats to put a price or value on the cost of lost business functionality?
You are responsible for network and information security at a large hospital. It is a significant concern that any change to any patient record can be easily traced back to the person who made that change. What is this called?
You are an Incident manager in Orangesect.Inc. You have been tasked to set up a new extension of your enterprise. The networking, to be done in the new extension, requires different types of cables and an appropriate policy that will be decided by you. Which of the following stages in the Incident handling process involves your decision making?
A project plan includes the Work Breakdown Structure (WBS) and cost estimates. Which of the following are the parts of a project plan?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following documents is necessary to continue the business in the event of disaster or emergency?
An organization monitors the hard disks of its employees' computers from time to time. Which policy does this pertain to?
In which of the following DRP tests does a business unit management meet to review the plan?
Which of the following processes involves reducing the risk until it reaches a level acceptable to an organization?
Which of the following system security policies is used to address specific issues of concern to the organization?
Which of the following are some of the parts of a project plan?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following procedures is designed to enable security personnel to identify, mitigate, and recover from malicious computer incidents, such as unauthorized access to a system or data, denial-of-service attacks, or unauthorized changes to system hardware, software, or data?
Which of the following are common applications that help in replicating and protecting critical information at the time of disaster?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following TCB techniques involves viewing system components at a high level and ignoring or segregating its specific details?
Which of the following techniques is an encryption method that uses public-key encryption to encrypt and digitally sign e-mail messages during communication between e-mail clients?
Which of the following terms describes the determination of the effect of changes to the
information system on the security of the information system?
You work as the project manager for Bluewell Inc. Your project has several risks that will affect several stakeholder requirements. Which project management plan will define who will be available to share information on the project risks?
John, a novice web user, makes a new e-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks? Each correct answer represents a complete solution. Choose all that apply.
Which of the following control measures are considered while creating a disaster recovery plan?
Each correct answer represents a part of the solution. Choose three.
Which of the following cryptographic system services assures the receiver that the received message has not been altered?
Which of the following security procedures is NOT related to the SDLC's disposition?
Which of the following is prepared by the business and serves as a starting point for producing the IT Service Continuity Strategy?
Which of the following processes helps to quantify the impact of potential threats to put a price or value on the cost of lost business functionality?
The Incident handling process implemented in an enterprise is responsible to deal with all the incidents regarding the enterprise. Which of the following procedures will be involved by the preparation phase of the Incident handling process?
You are responsible for network and information security at a large hospital. It is a significant concern that any change to any patient record can be easily traced back to the person who made that change. What is this called?
Drag and drop the appropriate team names in front of their respective responsibilities.
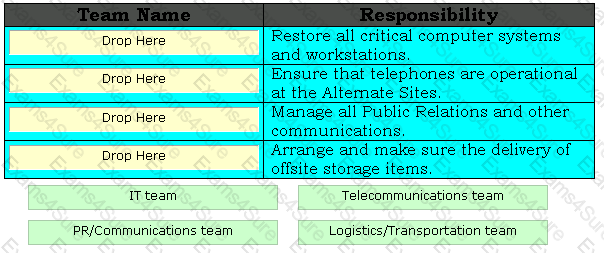
Which of the following BCP teams assesses the damage of the disaster in order to provide the estimate of the time required to recover?
Which of the following parts of BS 7799 covers risk analysis and management?
You work as a senior project manager in SoftTech Inc. You are working on a software project using configuration management. Through configuration management, you are decomposing the verification system into identifiable, understandable, manageable, traceable units that are known as Configuration Items (CIs). According to you, which of the following processes is known as the decomposition process of a verification system into Configuration Items?
Which of the following processes acts as a control measure that provides some amount of
protection to the assets?
Which of the following contract types is described in the statement below?
"The seller is reimbursed for all allowable costs for performing the contract work, and receives a fixed payment calculated as a percentage for the initial estimated project costs."


TESTED 17 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.