Performing CyberOps Using Core Security Technologies (CBRCOR)
Last Update 1 day ago
Total Questions : 139
Performing CyberOps Using Core Security Technologies (CBRCOR) is stable now with all latest exam questions are added 1 day ago. Incorporating 350-201 practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the Performing CyberOps Using Core Security Technologies (CBRCOR) exam format, identifying knowledge gaps, applying theoretical knowledge in Cisco practical scenarios, you are setting yourself up for success. 350-201 exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
350-201 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through 350-201 dumps allows you to practice pacing yourself, ensuring that you can complete all Performing CyberOps Using Core Security Technologies (CBRCOR) exam questions within the allotted time frame without sacrificing accuracy.
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the playbook to mitigate the threat. What is the first action for the incident response team?
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
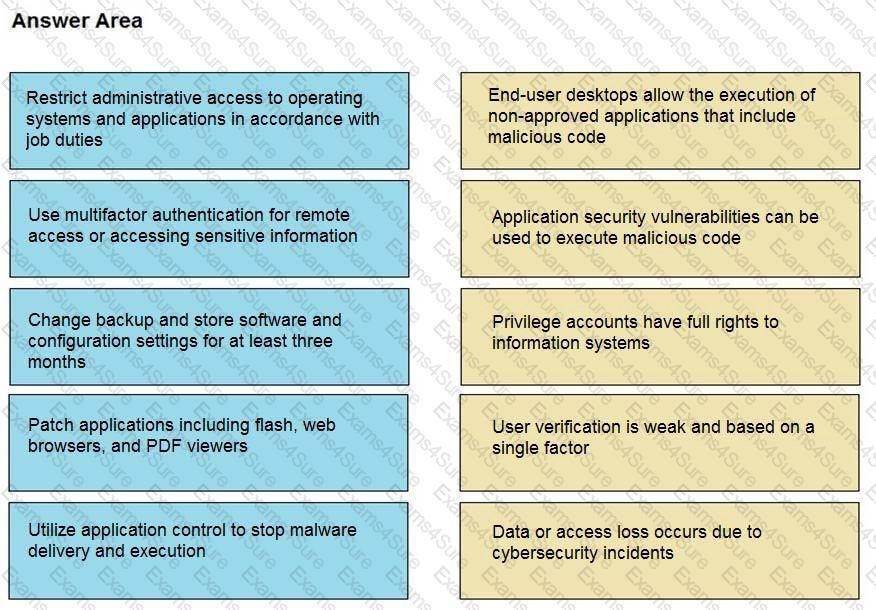
Drag and drop the mitigation steps from the left onto the vulnerabilities they mitigate on the right.
An organization had a breach due to a phishing attack. An engineer leads a team through the recovery phase of the incident response process. Which action should be taken during this phase?
A SIEM tool fires an alert about a VPN connection attempt from an unusual location. The incident response team validates that an attacker has installed a remote access tool on a user’s laptop while traveling. The attacker has the user’s credentials and is attempting to connect to the network.
What is the next step in handling the incident?
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
A patient views information that is not theirs when they sign in to the hospital’s online portal. The patient calls the support center at the hospital but continues to be put on hold because other patients are experiencing the same issue. An incident has been declared, and an engineer is now on the incident bridge as the CyberOps Tier 3 Analyst. There is a concern about the disclosure of PII occurring in real-time. What is the first step the analyst should take to address this incident?
Refer to the exhibit.
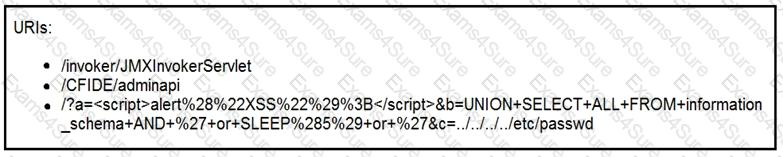
At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
An analyst wants to upload an infected file containing sensitive information to a hybrid-analysis sandbox. According to the NIST.SP 800-150 guide to cyber threat information sharing, what is the analyst required to do before uploading the file to safeguard privacy?
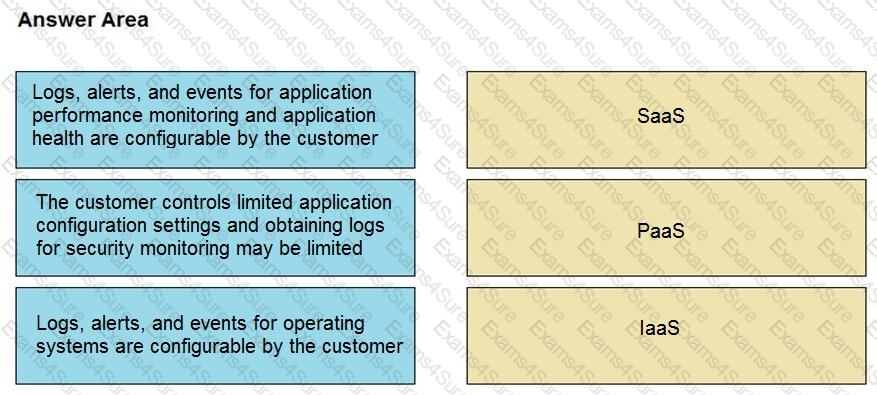
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.
The network operations center has identified malware, created a ticket within their ticketing system, and assigned the case to the SOC with high-level information. A SOC analyst was able to stop the malware from spreading and identified the attacking host. What is the next step in the incident response workflow?
Employees receive an email from an executive within the organization that summarizes a recent security breach and requests that employees verify their credentials through a provided link. Several employees report the email as suspicious, and a security analyst is investigating the reports. Which two steps should the analyst take to begin this investigation? (Choose two.)
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high. Which step should be taken to continue the investigation?
An engineer is moving data from NAS servers in different departments to a combined storage database so that the data can be accessed and analyzed by the organization on-demand. Which data management process is being used?
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
An organization had several cyberattacks over the last 6 months and has tasked an engineer with looking for patterns or trends that will help the organization anticipate future attacks and mitigate them. Which data analytic technique should the engineer use to accomplish this task?
Refer to the exhibit.
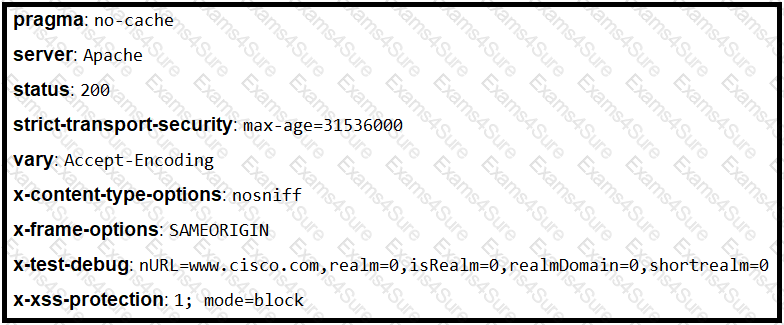
Where is the MIME type that should be followed indicated?


TESTED 12 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.