Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
Last Update 3 days ago
Total Questions : 363
Developing Applications using Cisco Core Platforms and APIs (DEVCOR) is stable now with all latest exam questions are added 3 days ago. Incorporating 350-901 practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the Developing Applications using Cisco Core Platforms and APIs (DEVCOR) exam format, identifying knowledge gaps, applying theoretical knowledge in Cisco practical scenarios, you are setting yourself up for success. 350-901 exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
350-901 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through 350-901 dumps allows you to practice pacing yourself, ensuring that you can complete all Developing Applications using Cisco Core Platforms and APIs (DEVCOR) exam questions within the allotted time frame without sacrificing accuracy.
Refer to the exhibit.

A network engineer created a simple Python Flask application but must incorporate a CSRF token. Which code snippet must be added in the blank in the script to manually incorporate the token?
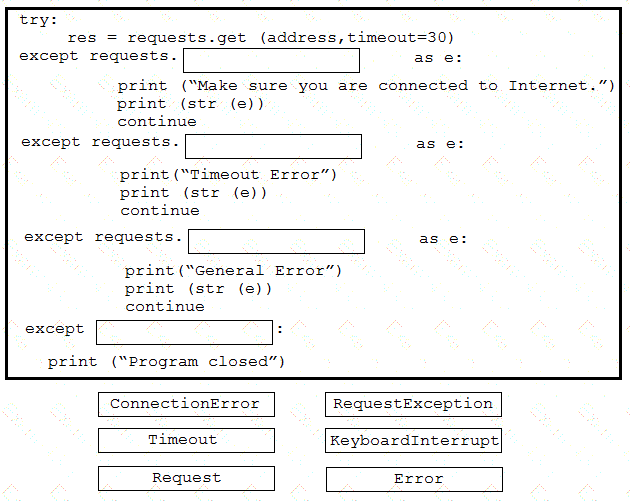
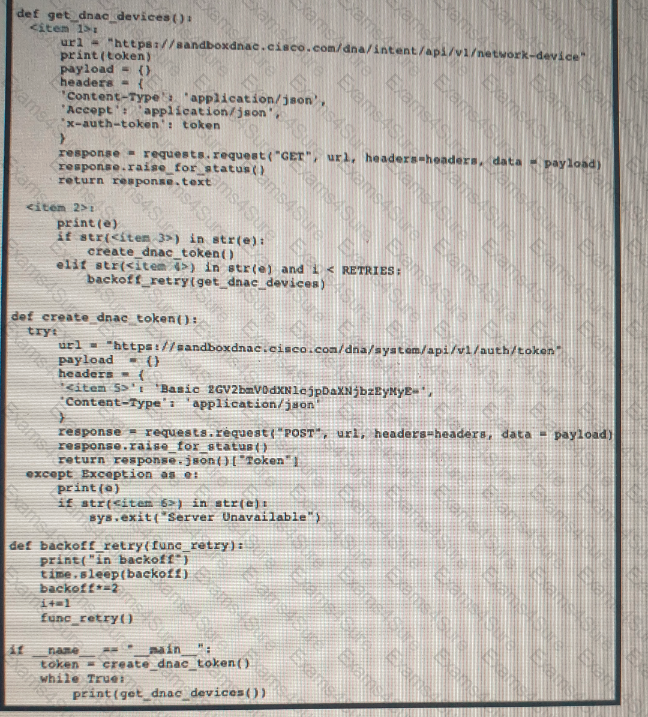
A developer is creating a Python script to catch errors using REST API calls and to aid in debugging. Drag and drop the code from the bottom onto the box where the code is missing to implement control flow for REST API errors. Not all options are used.
Refer to the exhibit.
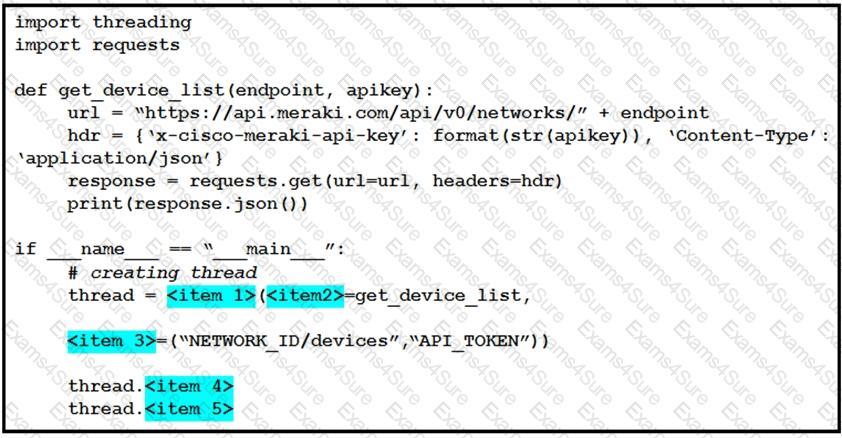
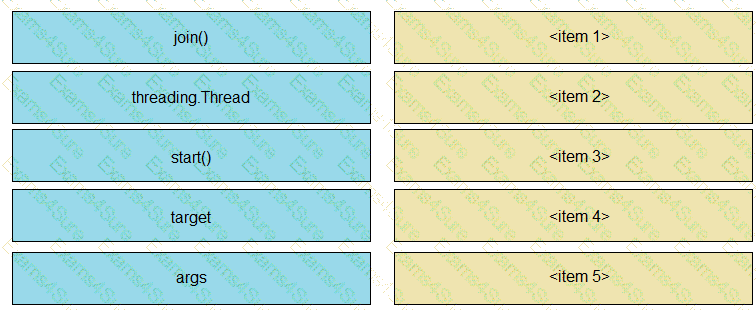
Python threading allows a developer to have different parts of a program run concurrently and simplify a design. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a thread instance.
Refer to the exhibit.
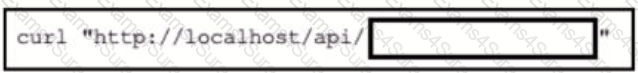
An application's REST API GET call is tested to the inventory database. Which missing code must be included to limit
the number of values that are returned from the query to 20?
Which configuration stop must be performed on a Cisco IOS XE device to present collected data in Cisco DNA Center?
A developer is working on a live project and must apply a new feature. After the commit,the manager informs the team that the wrong file was applied. The developer must undo the single commit and apply the file with the name feature-App-UXU1411841916AD
D.
Which command must the developer use?Drag and drop the code from the bottom onto the box where the code is missing to create a new Cisco Webex space and attach a previously configured bot named 'sampleBot'. Not all options are used.

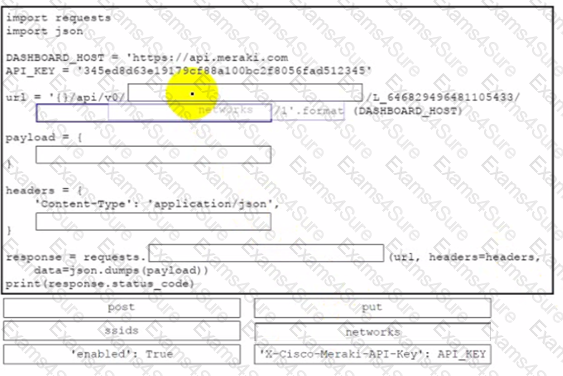
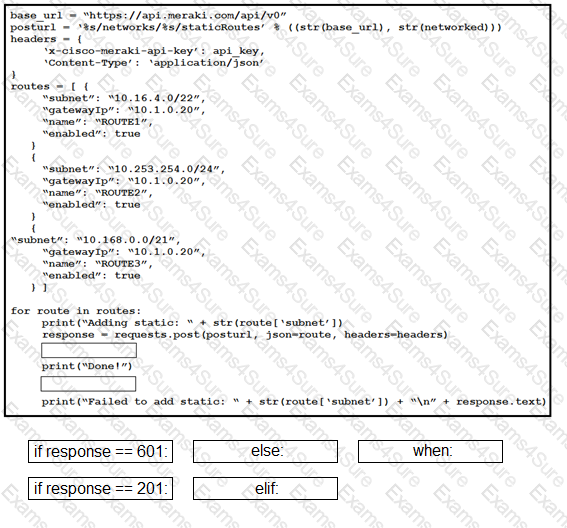
Drag and drop the code from the bottom onto the box where the code is missing to enable an SSID by using the Cisco Meraki Dashboard API. Not all options are used.
Refer to the exhibit.
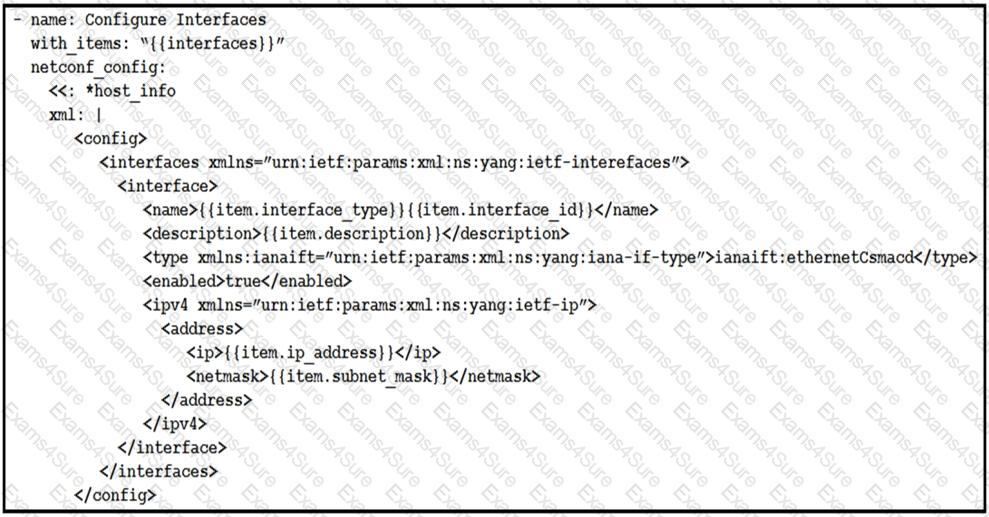
The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
Drag and drop the code from the bottom onto the box where the code is missing to create a Puppet manifest that implements an NTP configuration when applied to a device in the master inventory. Not all options are used.
An application is made up of multiple microservices, each communicating via APIs. One service is beginning to be a bottleneck for the application because it can take a lot of time to complete requests. An engineer tried adding additional instances of this service behind the load balancer, but it did not have any effect. Which application design change must be implemented m this scenario?
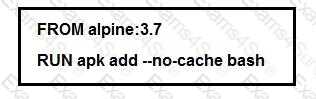
A developer has created a local Docker alpine image that has the image ID 'dockapp432195596ffr' and tagged as ‘new’. Which command creates a running container based on the tagged image, with the container port 80 bound to port 8080 on the host?
A developer must recommend an appropriate tool to deploy a configuration to hundreds of servers. The configuration management solution must meet these requirements.
• The servers must initiate the connection to obtain updates
• The configuration must be defined in a declarative style
Which tool should be used?
Refer to the exhibit Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
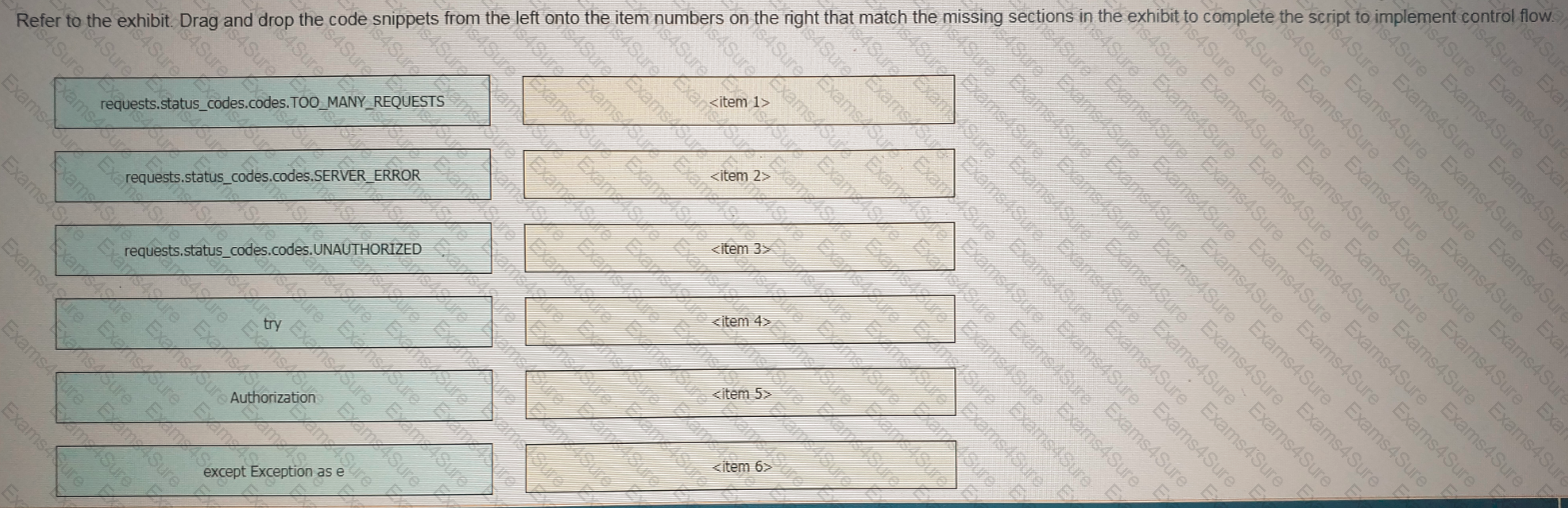
Refer to the exhibit.
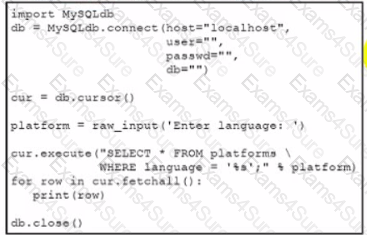
Which action should be performed to avoid an SQL injection attack?
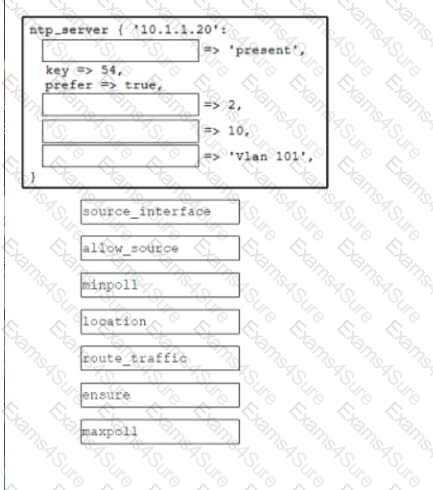
Which Puppet manifest changes the NTP server and generates the traffic from VLAN 15?
A)

B)

C)

D)

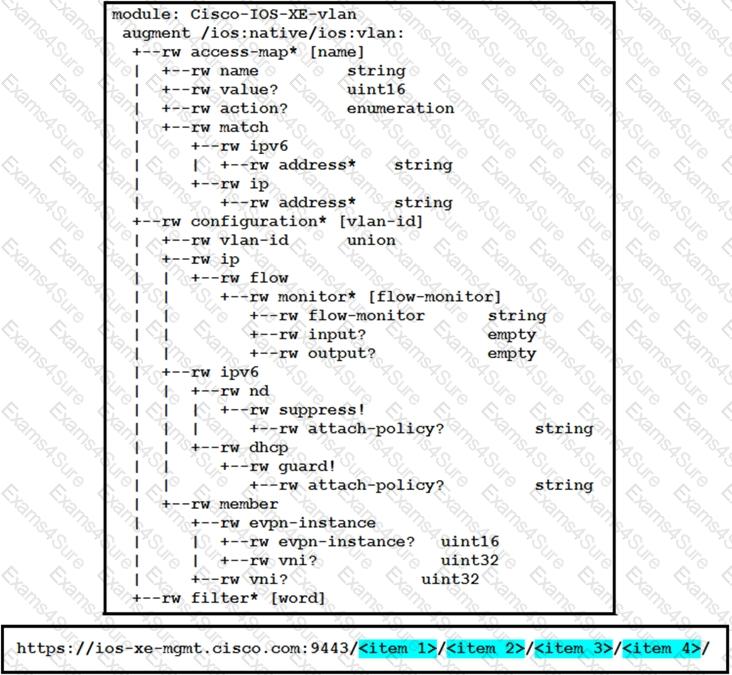
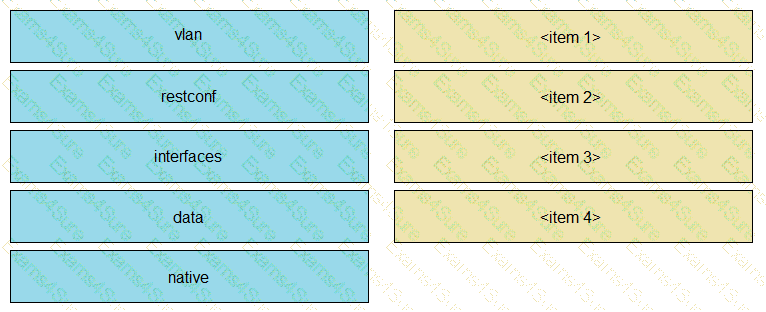
Refer to the exhibit. Drag and drop parts of the URL from the left onto the item numbers on the right that match the missing sections in the exhibit to create the appropriate RESTCONF URL to query the VLAN configuration given this YANG model. Not all URL parts are used.
A heterogeneous network of vendors and device types needs automating for better efficiency and to enable future automated testing. The network consists of switches, routers, firewalls and load balancers from different vendors, however they all support the NETCONF/RESTCONF configuration standards and the YAML models with every feature the business requires. The business is looking for a buy versus build solution because they
cannot dedicate engineering resources, and they need configuration diff and rollback functionality from day 1.
Which configuration management for automation tooling is needed for this solution?
Click on the resource lab in the top left comer to view resources to help with this question An engineer is managing a data center with 6000 Cisco UCS servers installed and running The engineer is asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB Drag and drop the code from the bottom onto the blanks in the code snippet to construct a REST API call to accomplish this task Not all options are used.

A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls. Which approach enhances the responsiveness and performance of the API?
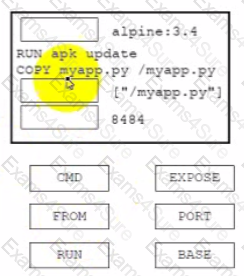
Drag and drop the code from the bottom onto the box where the code is missing on the Dockerfile to containerize an application that listens on the specified TCP network port at runtime. Not all options are used.
Drag and drop the code from the bottom onto the box where the code is missing to configure a router that runs Cisco IOS XE by using RESTCON
F.
The API call is made to the management URL of the IOS XE device and on a registered port number. Errors that are caught during HTTP operation are registered. Not all options are used.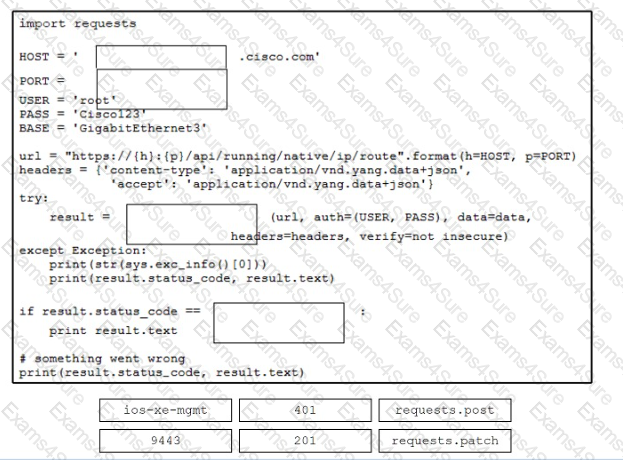
Refer to the exhibit.
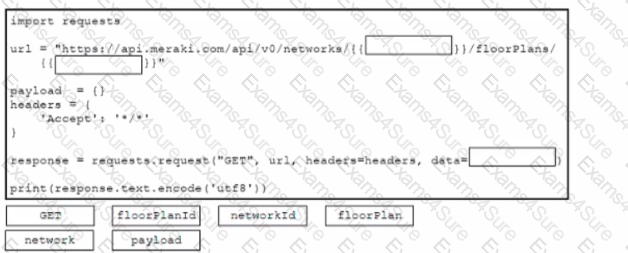
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that will retrieve location data Not all options are used.
Refer to the exhibit.
Which additional line results in the output of Test 1 upon execution of the docker run --rm devnet 1 command in a Dockerfile with this content?
Refer to the exhibit.
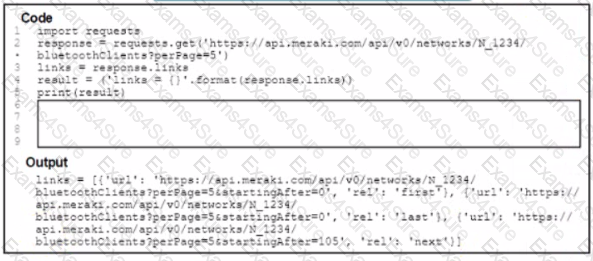
A Python script has these requirements
• Retrieve a list of Bluetooth clients seen by the access pants on a network.
• Print the content of the response
• Retrieve the next page only if it is available in the response headers
What must be added where the code is missing to get the remaining pages by using the next link from the link response header of the last request?
A)
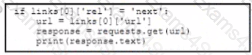
B)

C)
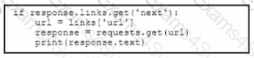
D)
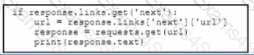
An engineer is developing a web-based application that will be used as a central repository for the HR department The application needs to authenticate user access and encrypt communication. Drag and drop the steps from the left into the order on the right to install an application-specific SSL certificate.
Which database type should be used to store data received from model-driven telemetry?
Refer to the exhibit.
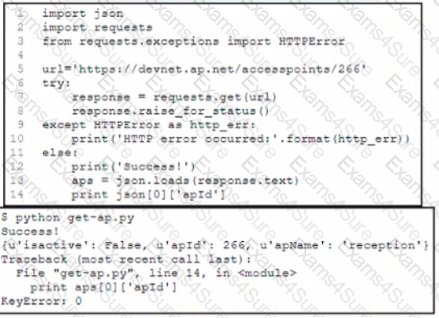
A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points The developer is retrieving an access point ID by using a REST API The output indicates that there was a KeyError when parsing the JSON response. What returns the expected output of 266 at line 14?
A)

B)

C)

D)
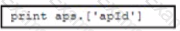
An Etag header is included in the HTTP response for an API resource. What are two benefits of using the value of the Etag for future interactions involving the same API resource? (Choose two.)
Refer to the exhibit.
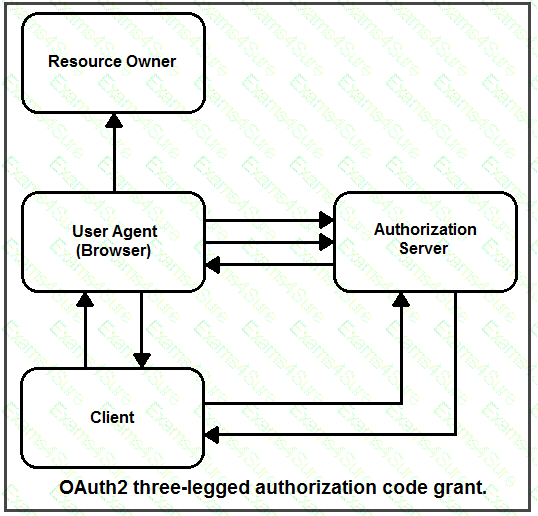
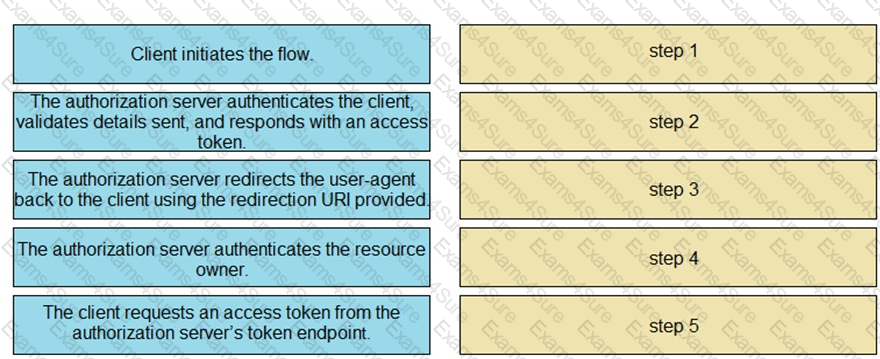
Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Why is end-to-end encryption deployed when exposing sensitive data through APIs?
Refer to the exhibit.
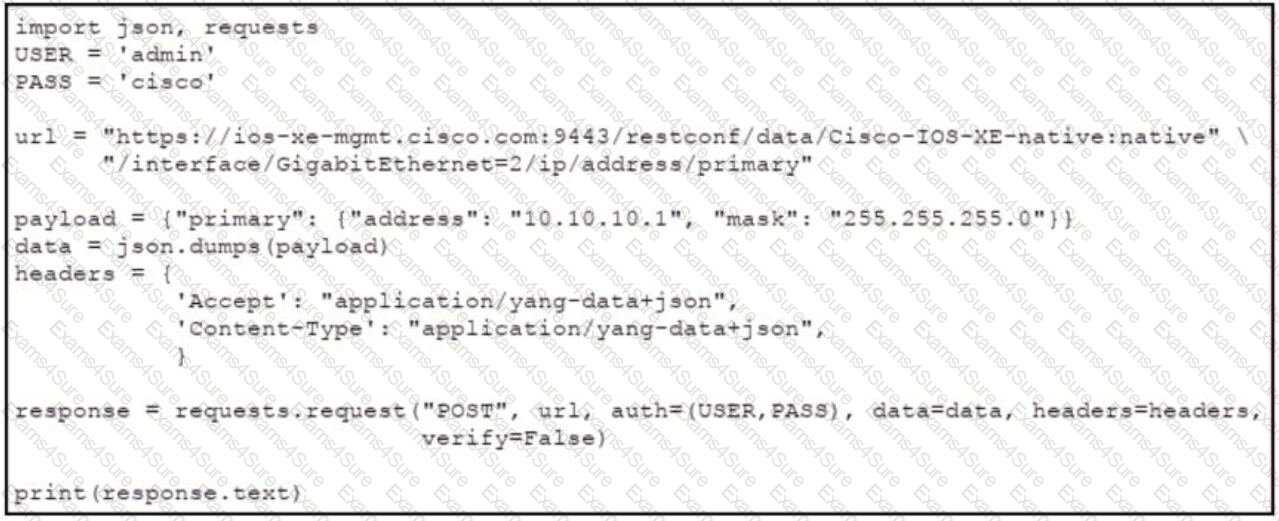
An engineer needs to change the IP address via RESTCOMF on interface GigabitEthernet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?
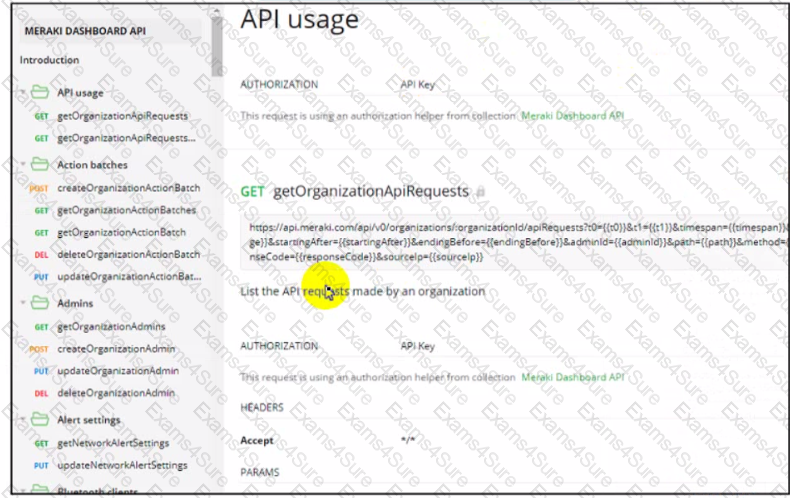
A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count. What needs to be built as a prerequisite?
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
A developer is working on a new feature in a branch named 'newfeay000222118' and the current working primary branch is named 'pnm409024967' The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must Be used?
A)
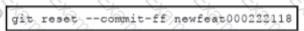
B)

C)

D)

Drag and drop the code from the bottom onto the box where the code is missing to create a new IKEv2 policy Not all options are used

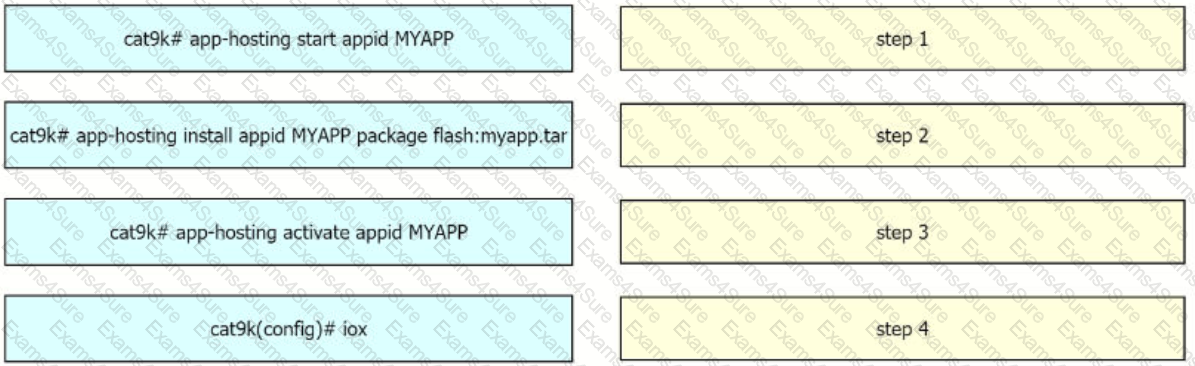
Drag and drop the steps from the left into the order on the right to configure and install a container on a Cisco Catalyst 9000 Series Switch.
Refer to the exhibit.
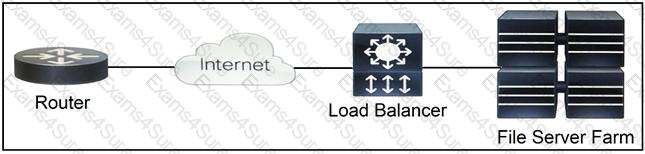
Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
Which two principles are included in the codebase tenet of the 12-factor app methodology? (Choose two.)
What securely stores and encrypts the API keys and tokens that are used for an application deployment?
How does the use of release packaging allow dependencies to be effectively managed during deployments?
Refer to the exhibit.
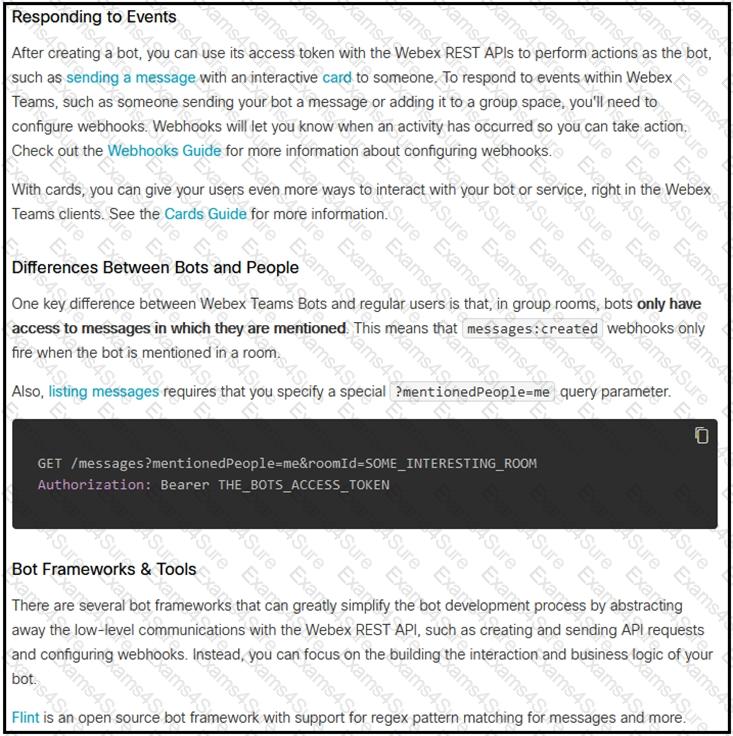
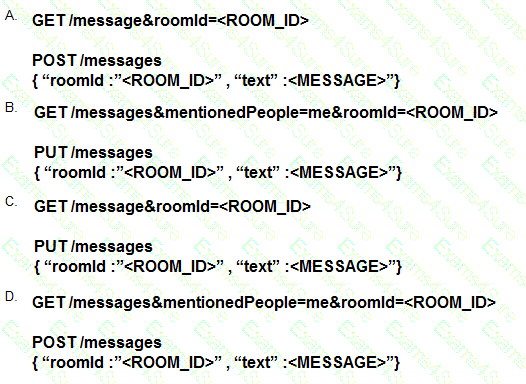
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
Refer to the exhibit.

A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server. When considering maintainability, which two changes must be made to the code? (Choose two.)
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?
Refer to the exhibit.
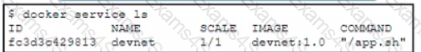
Refer to the exhibit A Docker swarm service is currently running m a local data center The service is hosting an HTML website it the container fads then the service becomes unavailable The design must meet these requirements
• The service must be highly available and resilient against a data center outage.
• The service must be accessible from a single URL
• The HTTP session must remain on the server from which the original request was sent
• Failure of the server must force the client to reconnect
Which two design approaches must be used to meet the requirements? (Choose two.)
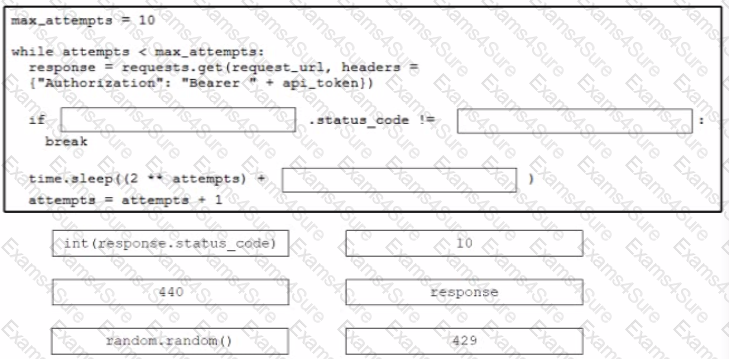
Drag and drop the code from the bottom onto the box where the code is missing to stop the REST API requests if a 'Too Many Requests" response is received Not all options are used.
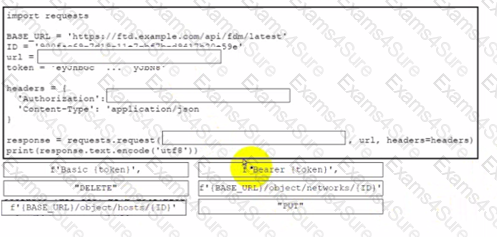
Drag and drop the code from the bottom onto the box where the code is missing to delete a host object by using the Cisco Firepower Device Manager API Not all options are used.
What is an effective logging strategy according 10 the 12-factor app tenets?
Refer to the exhibit.
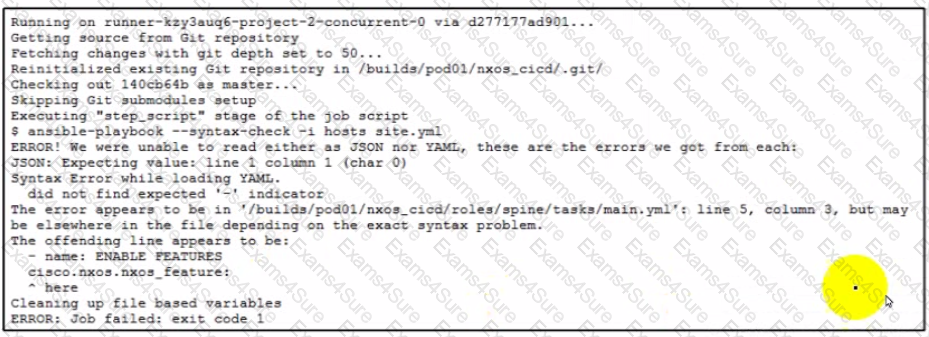
A network engineer developed an Ansible playbook and committed it to GitLab. A GitLab CI pipeline is started but immediately fails. What is the issue?
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.


TESTED 10 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.