Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Last Update 4 days ago
Total Questions : 131
Dive into our fully updated and stable 300-215 practice test platform, featuring all the latest CyberOps Professional exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our free CyberOps Professional practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 300-215. Use this test to pinpoint which areas you need to focus your study on.
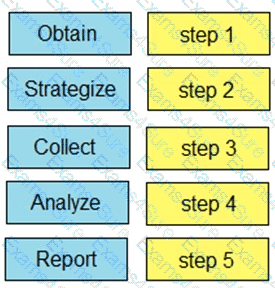
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.
An engineer must advise on how YARA rules can enhance detection capabilities. What can YARA rules be used to identify?
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?


An organization fell victim to a ransomware attack that successfully infected 256 hosts within its network. In the aftermath of this incident, the organization's cybersecurity team must prepare a thorough root cause analysis report. This report aims to identify the primary factor or factors that led to the successful ransomware attack and to develop strategies for preventing similar incidents in the future. In this context, what should the cybersecurity engineer include in the root cause analysis report to demonstrate the underlying cause of the incident?
During an overnight shift, a cybersecurity team at a global trading firm detects irregular activity The network intrusion system flags an encrypted traffic spike from high-value transaction servers to an anonymous Tor exit node Simultaneously, internal surveillance tools report unusual database queries and access patterns resembling exfiltration techniques Which focused action should the team take first to analyze and address these potential security threats?
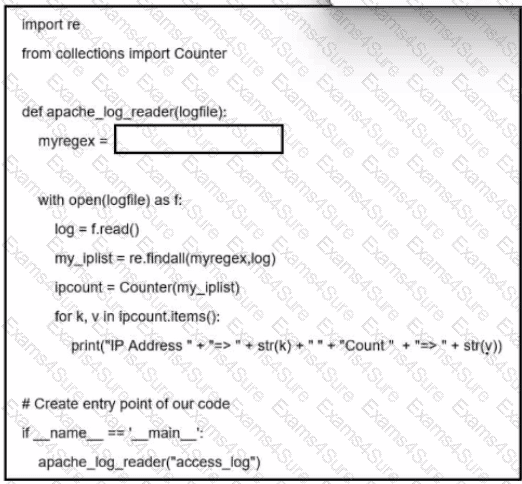
Refer to the exhibit. A network administrator creates an Apache log parser by using Python. What needs to be added in the box where the code is missing to accomplish the requirement?


TESTED 28 Feb 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.