CIW Web Foundations Associate
Last Update 6 days ago
Total Questions : 82
1D0-610 is stable now with all latest exam questions are added 6 days ago. Just download our Full package and start your journey with CIW Web Foundations Associate certification. All these CIW 1D0-610 practice exam questions are real and verified by our Experts in the related industry fields.
A family member has just sent you an e-mail message that contains highly personal details about a family matter. The message was sent to your company e-mail address. The family member has requested that you respond with your ideas about how to resolve the situation. Which of the following is a reason for you to call your family member and discuss the matter over the phone instead?
A friend just sent you a link to a Facebook page with information that you find very useful. You want to be able to recall the site in the future from your desktop computer, or from your mobile device while away from your desk. Which is the best approach?
You are distributing a large video game file using BitTorrent. First, you upload the initial file and make it available via a central server called a tracker. Other users can then connect to the tracker and download the file. Each user who downloads the file makes it available to other users to download. The use of BitTorrent significantly reduces the original provider’s hardware and bandwidth resource costs. BitTorrent is an example of what type of network?
The Internet has enabled many new anti-social activities, such as online stalking, cyber bullying, and addiction to solitary online activities. Which choice is the most feasible way for schools and parents to reduce cyber bullying?
You received an e-mail message on which several other individuals were copied. You want to respond to this message in a way that will include everyone who was copied on the original message. You can accomplish this by using which action?
Which type of attack is a form of social engineering in which an attacker attempts to steal personal or confidential information by sending e-mail that lures unsuspecting victims to log in to an authentic-looking but imposter Web site?
You want to enable wireless security on your Android device and your Linux system. Which of the following is a disadvantage of Wired Equivalent Privacy (WEP)?
Proprietary information for your company’s online business was released to a competitor. Which of the following preventative measures should your company take to ensure that its proprietary information is protected in the future?
Marsha has been hired by XYZ, Inc., to update the company Web site. Marsha discovers that the existing Web pages were structured using tables. Marsha needs to explain to XYZ why the Web site needs to be recoded in HTML5 with CSS controlling the structure of the document. What is the most important reason for using HTML5 and CSS?
You are the technology coordinator for a small multi-national corporation with offices in Los Angeles, New York, Tokyo and London. You have been asked to coordinate a live and interactive meeting that will allow executives from each of the offices to meet virtually and share presentations. What is the best way to achieve this desired goal?
You are creating a style sheet to format your Web pages. For the page background color, you enter the hexadecimal code FF0000. What color will the page background be when you apply this style?
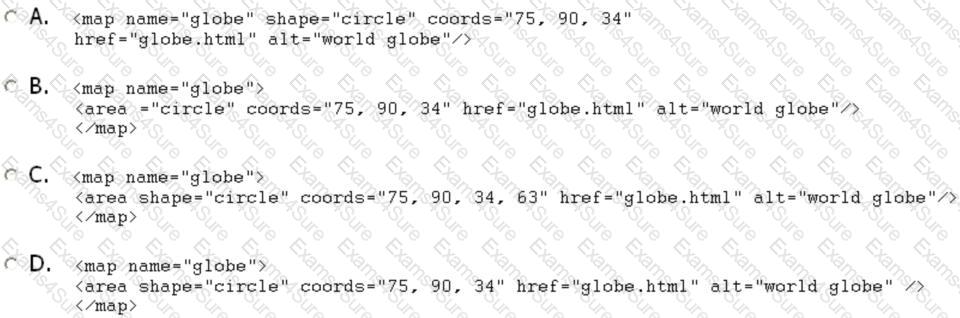
To define a circle-shaped hot-spot for an image map, which of the following code fragments would you use?


TESTED 29 Apr 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.