Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Last Update 1 day ago
Total Questions : 476
Dive into our fully updated and stable 200-201 practice test platform, featuring all the latest CyberOps Associate exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our free CyberOps Associate practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 200-201. Use this test to pinpoint which areas you need to focus your study on.
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
What is the impact of false negative alerts when compared to true negative alerts?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
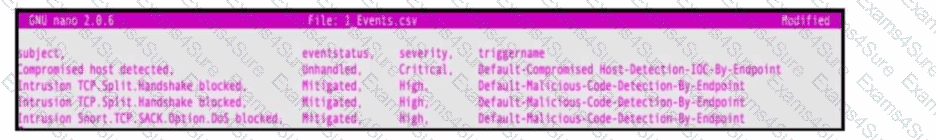
Refer to the exhibit. An engineer must map these events to the source technology that generated the event logs. To which technology do the generated logs belong?
A data privacy officer at a marketing firm has received a request from a former client to delete all personally sensitive information held by the company. The firm operates globally and follows international data protection standards. The only information retained about the client is a unique customer ID, "051473912", which is not directly tied to the name, address, or any other identifiable details. Which action should the data privacy officer take?
A large load of data is being transferred to an external destination via UDP 53 port. Which obfuscation technique is used?


TESTED 01 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.