Implementing Secure Solutions with Virtual Private Networks (SVPN)
Last Update 1 day ago
Total Questions : 175
Dive into our fully updated and stable 300-730 practice test platform, featuring all the latest CCNP Security exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our free CCNP Security practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 300-730. Use this test to pinpoint which areas you need to focus your study on.
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose two.)
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2 packet will contain details of the exchange?
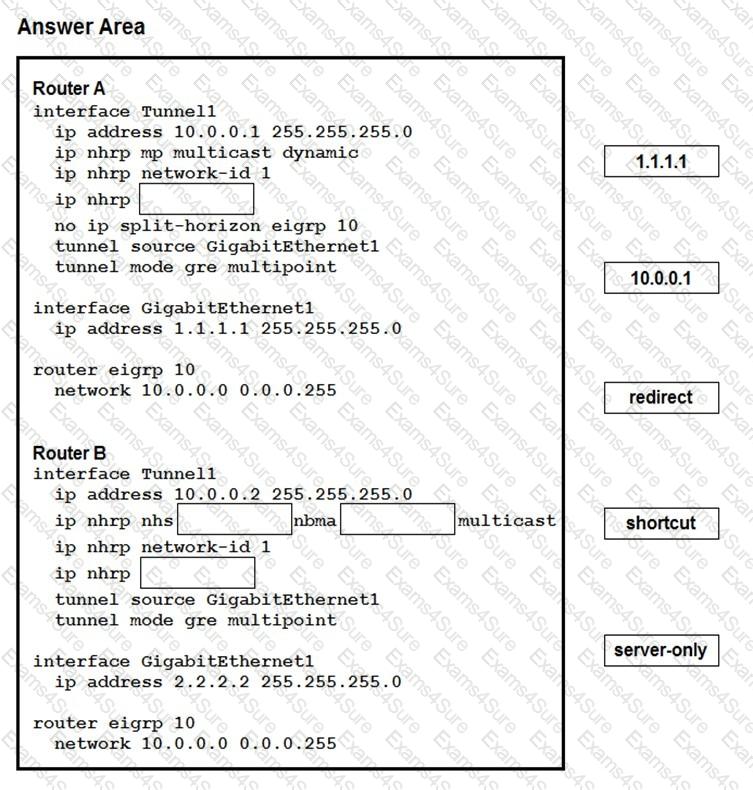
Drag and drop the correct commands from the night onto the blanks within the code on the left to implement a design that allow for dynamic spoke-to-spoke communication. Not all comments are used.
Refer to the exhibit.
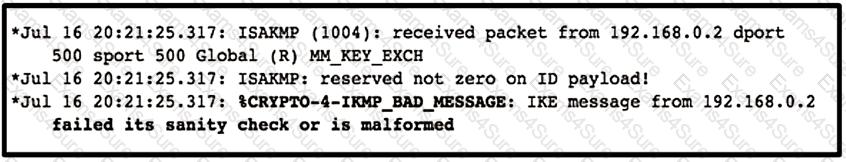
Which type of mismatch is causing the problem with the IPsec VPN tunnel?
Refer to the exhibit.

An SSL client is connecting to an ASA headend. The session fails with the message “Connection attempt has timed out. Please verify Internet connectivity.” Based on how the packet is processed, which phase is causing the failure?
Refer to the exhibit.
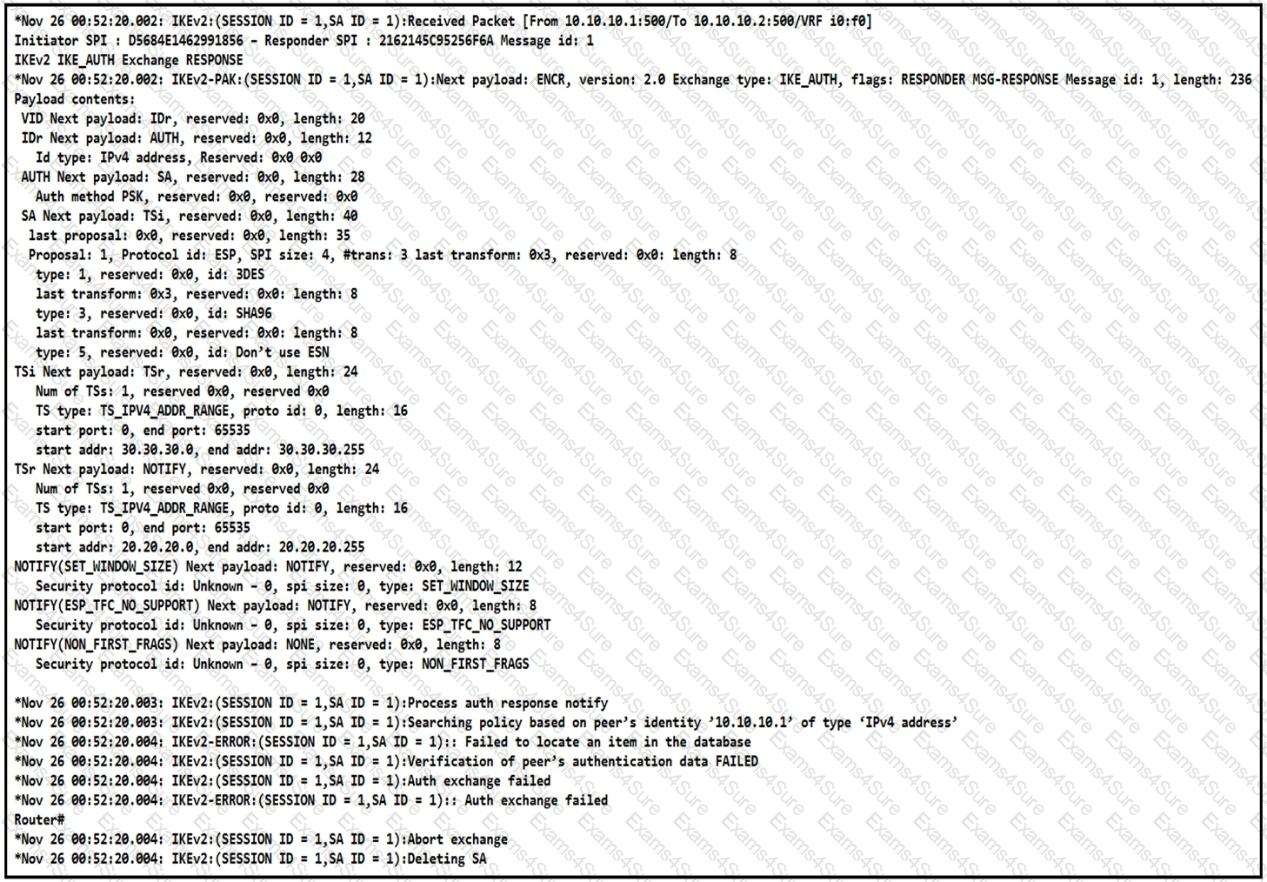
The IKEv2 site-to-site VPN tunnel between two routers is down. Based on the debug output, which type of mismatch is the problem?
Which command is used to troubleshoot an IPv6 FlexVPN spoke-to-hub connectivity failure?
Which two commands help determine why the NHRP registration process is not being completed even after the IPsec tunnel is up? (Choose two.)
Which technology is used to send multicast traffic over a site-to-site VPN?


TESTED 01 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.