Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
Last Update 5 days ago
Total Questions : 217
Huawei Certified ICT Professional - Constructing Infrastructure of Security Network is stable now with all latest exam questions are added 5 days ago. Incorporating H12-721 practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the Huawei Certified ICT Professional - Constructing Infrastructure of Security Network exam format, identifying knowledge gaps, applying theoretical knowledge in Huawei practical scenarios, you are setting yourself up for success. H12-721 exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
H12-721 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through H12-721 dumps allows you to practice pacing yourself, ensuring that you can complete all Huawei Certified ICT Professional - Constructing Infrastructure of Security Network exam questions within the allotted time frame without sacrificing accuracy.
Which of the following protocol messages cannot be propagated in an IPSec tunnel by default?
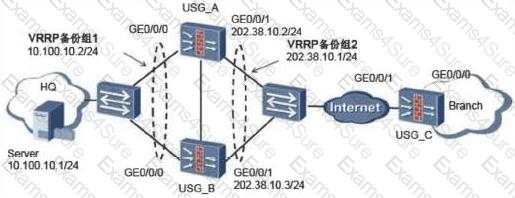
87. The SSL VPN scenario under dual-system hot standby is shown in the following figure. The administrator has enabled the SSL network extension function. The following is about the configuration of the SSL VPN function.
The following figure shows the L2TP over IPSec application scenario. The client uses the pre-shared-key command to perform IPSec authentication. How should the IPSec security policy be configured on the LNS?
Three physical interfaces have been added to the link-group group. When any one of the interfaces fails, what are the following descriptions correct?
The Haiwei Secoway VPN client initiates an L2TP connection. The source port of the L2TP packet is 1710 and the port 1710 of the destination port.
When the ip-link link health check is performed, if it is unable to receive the message several times in the absence of the link, it will be considered as a link failure.
134. Which of the following is the connection status data to be backed up in the HRP function?
Which of the following statements is correct about the IKE main mode and the aggressive mode?
IPSec NAT traversal does not support IKE main mode, aggressive mode IP address + pre-shared key mode authentication, because pre-shared key mode authentication needs to extract the source IP address in the IP address to find the pre-shared key corresponding to this address. . The address change caused by the presence of NAT prevents the device from finding the pre-shared key.
The network of an enterprise is as follows. At this time, server A cannot access the web service of server
B.
The administrator performs troubleshooting and finds that there is no problem in the routing mode of firewallA.
The corresponding routing table has been established, but the firewall mode of firewall A is set. error. What is the method used by the administrator to troubleshoot the problem?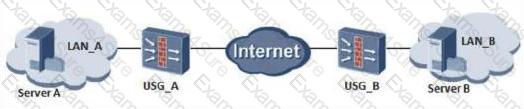
The topology diagram of the BFD-bound static route is as follows: The administrator has configured the following on firewall A: [USG9000_A] bfd [USG9000_A-bfd] quit [USG9000_A] bfd aa bind peer-ip 1.1.1.2 [USG9000_A- Bfd session-aa] discriminator local 10 [USG9000_A-bfd session-aa] discriminator remote 20 [USG9000_A-bfd session-aa] commit [USG9000_A-bfd session-aa] quit What are the correct statements about this segment?

In the application scenario of IPSec traversal by NAT, the active initiator of the firewall must configure NAT traversal, and the firewall at the other end can be configured without NAT traversal.
On the following virtual firewall network, the USG unified security gateway provides leased services to the enterprise. The VPN instance vfw1 is leased to enterprise
A.
The networking diagram is as follows. The PC C of the enterprise A external network user needs to access the intranet DMZ area server B through NAT. To achieve this requirement, what are the following key configurations?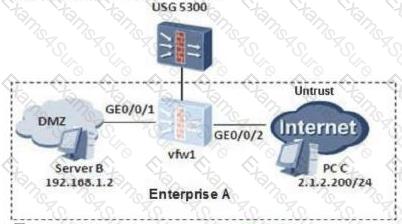
An enterprise network is as follows. Firewall A and firewall B establish an IPSec VPN. After the IPSec configuration is complete, the administrator needs to test the connectivity of the IPSec VPN. Generally, the firewall needs to simulate the traffic of the server A to access the intranet server
B.
The administrator can use which of the following ping commands.
The SSL VPN authentication login is unsuccessful and the message "Bad username or password" is displayed. Which one is wrong?
The classification of cyber-attacks includes traffic-based attacks, scanning and snooping attacks, malformed packet attacks, and special packet attacks.
Networking as shown in the figure: PC1--USG--Router--PC2. If PC1 sends a packet to PC2, what are the three modes for the USG to process fragmented packets?
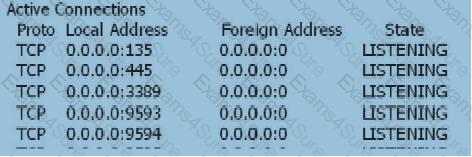
When the user's SSL VPN has been successfully authenticated, the user cannot access the Web-link resource. On the Web server, view the information as follows: netstat -anp tcp With the following information, which of the following statements is correct?
What are the scenarios in which the USG series firewall service port sends gratuitous ARPs when the following configurations are performed?
About load balancing, the following configuration is available: [USG] slb enable [USG]slb [USG-slb] rserver 1 rip 10.1.1.3 weight 32 [USG-slb] rserver 2 rip 10.1.1.4 weight 16 [USG-slb] rserver 3 rip 10.1.1.5 weight 32 [USG-slb] group test [USG-slb-group-test]metric srchash [USG-slb-group-test] add rserver 1 [USG-slb-group-test] add rserver 2 [ USG-slb-group-test] add rserver 3 Which of the following statements is correct?
When the user logs in to the virtual gateway web page and prompts “Cannot display web page”, what is the possible cause of the failure?
For IP-MAC address binding, packets with matching IP and MAC address will enter the next processing flow of the firewall. Packets that do not match IP and MAC address will be discarded.
The first packet discarding technology of Huawei Anti-DDoS devices can defend against attack packets that continuously change the source IP address or source port number. The following is incorrect about the first packet discarding technology?
The DHCP snooping function needs to maintain the binding table. What are the contents of the binding table?
Using the virtual firewall technology, users on the two VPNs can log in to their private VPNs through the Root VFW on the public network to directly access private network resources. What are the following statements about the characteristics of the VPN multi-instance service provided by the firewall?
Site to Site IPSec VPN negotiation failed. Which of the following should be checked? 1. Network connectivity issues; 2. View the establishment of IKE phase 1 security associations and related configurations; 3. View the establishment of IKE phase 2 security associations and related configurations; 4. See if the security ACLs at both ends mirror each other.


TESTED 05 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.