HCIE-Datacom V1.0
Last Update 3 days ago
Total Questions : 610
H12-891_V1.0 is stable now with all latest exam questions are added 3 days ago. Just download our Full package and start your journey with Huawei HCIE-Datacom V1.0 certification. All these Huawei H12-891_V1.0 practice exam questions are real and verified by our Experts in the related industry fields.
The RSTP protocol provides a variety of protection functions, such as when the edge port is configured as a protection state, the edge port receives the BPDU packet processing method;
After you divide an interface of the firewall into the Untrust security domain, the interface belongs to the Untrust zone and no longer belongs to the Local zone.
When configuring the source NAT and having no pat configuration parameters, which of the following statements is true?( Radio) A Perform destination IP address and destination port translation
B.
Only source P address translation occursC.
Only destination IP address translation occursD.
Simultaneous source P address and source port translationIn the following topology diagram, R1 can access the Internet through R2 and R3, R1 and R2, R1 and R1 An EGP connection is established between R3 , and R2R3 belongs to the same AS, each via BGP Publishing a default route that requires R1 to visit lnternet's traffic preference R2, can the following practices be achieved?
You expect to deploy multicast video applications on your private, on-premises network. To achieve this, you need to have a private multicast IP address in your network . So which range of IP addresses can be used?( Single choice questions).
A company's two-layer phase network architecture as shown in the figure, when the engineer is configured to find that the business between departments can not communicate, through the command to view the status of the equipment as follows, please determine the possible causes?
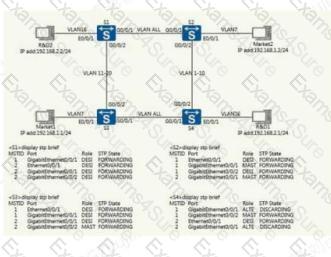
Huawei's two switches SWA and SWB are connected together by 7 Ethernet cables, and static link clustering is configured, and the corresponding port on the switch SWA is Ethernet 1/0/1 ?Ethernet1/0/2?Ethernet 1/0/3?Ethernet 1/0/4?Ethernet 1/0/5, Ethernet1/0/6, Ethernet 1/0/7, configured in order of port if the switch SWA, SWB supports only 6 ports per aggregation group
The following description of MP-BGP is incorrect?( Single choice questions).
The topology diagram and configuration are as follows, and now we hope that there is no buttoned route entry of 10033/32 in the Rl route table

By default, routers running IS-IS in broadcast networks have a period of seconds for DIS to send CSNP packets?
What is the security level for untrust zones in the USG Series firewalls? ( Radio).
In MPLSVPN, in order to distinguish between IPv4 prefixes that use the same address space, the RD value is added to the IPv4 address, and the following options are described correctly as ?
BGP EVPN does MAC address advertisement, ARP message advertisement, and IRB route advertisement for which BGP EVPN route is advertised?
The following statement about the VXLAN gateway is incorrect?( Single choice questions).
XLAN uses BGP EVPN to establish a tunnel, what type of message is used? ( Single choice questions).
When configuring ISIS zone authentication, which ISIS message will carry the authentication letter? ( Single choice questions).
What are the problems with manually creating static VXLAN tunnels in campus networks? Multi-select
The firewall has created some security zones by default, which of the following security zones does not exist by default on the firewall?( Radio).
As shown in the figure, PC1 and PC2 are hosts that belong to the same network segment, below about between PC1 and PC2 What are the correct descriptions of IPv6 neighbor states?

Because BGP is an EGP routing protocol, BGP routing policies can only be deployed between EBGP neighbors, and routing policies between IBGP neighbors are not valid.
Which of the following options can affect the establishment of IBGP neighbors?
If the receive cache of a switch's gigabit Ethernet interface is full, what protocol does the switch use to know that the remote interface delays sending data frames for a period of time?
The data results of a router are as follows, and the analysis conclusion is correct (single choice).

Both the CSNP packet of ISlS and the DD packet of OSPF have a role in the MA network, describing the role of the link state database summary, which is correct compared to the following statements of these two types of messages
Router HW enables OSPF and router HW has the role of ABR and is configured with abr-summary, then which class LSA Will it be aggregated?
SSH uses asymmetric encryption algorithms AES and DES to achieve security for data transmission, and uses HMAC to ensure the complete integrity of integer data
Which of the following attacks are DoS (Denial of servioe) attacks?( Multiple choice question)
For Layer 2 VPN technology, the following statement is correct? Multi-select
The following description of the characteristics of multi-instance CE is ?
Regarding BGP's recognized arbitrary attributes, which of the following descriptions is correct?
What is the field that the IPv6 header has similar to the IPv4 header "Type of Service" field?
The following description of 8021S deployment characteristics is correct?( Multiple choice question)
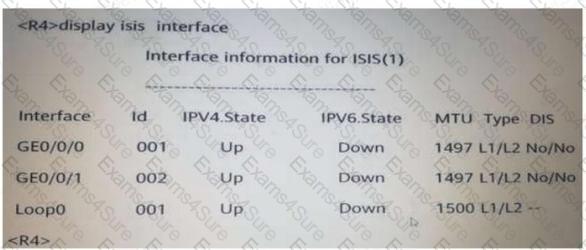
Based on the configuration shown in the figure below, it can be known that R4 has () interfaces advertised into IS-IS?
The following statement about IPSG technology is correct (single choice).
You are now troubleshooting a LAN, and you suspect that the error is due to a mismatch in the work mode. Which switch interface error indicates that the 10/100/100O IEE gigabit interface operating mode does not match?( Multiple choice questions).
What are the following correct statements about MUX VLANs?( Multiple select).
If you run PIM-SM in a multicast network, you need to build a multicast forwarding tree between the multicast source and the receiver to enable the receiver to receive the multicast effect, so what are the following options for the correct tree sketch for the build?
What information does this contain in a basic layer packet? (Multiple choice) A Data link layer header
B.
Upper-level dataC.
The network layer headerD.
path recordsE.
Network Layer TailWhat categories can ACLs be divided into?
A.
Advanced ACLsB.
Two-layer ACLC.
User-defined ACLsD.
Basic ACLA company deployed SSM multicast, in order to save the bandwidth consumption of multicast data in the LAN, the network administrator made the following configuration on the switch
The following description of BGP load sharing is wrong with ?( Multiple choice question)
Mainstream Layer 2 tunneling technologies include VXLAN TRILL, NVGB and MPLS.
The following statement about IPv6 Over VXLAN is wrong as ?( Single choice questions).
Huawei's two switch SWA, SWB is connected together through 7 Ethernets, and static route aggregation is configured, and the corresponding ports on the switch SWA are E1/0/1, E1/02, E1/0/3, E1/0/4, E1/ 0/5, E1/0/6, E1/0/7, configured sequentially as if switch SWA, SWB Each aggregation group supports only 6 ports.
In route-policy, what are the BGP attributes that can be used for the apply clause?
In a multicast network, what causes multicast traffic to not forward properly?
If the Interface Sticky MAC function is enabled, what is the number of MAC addresses that the interface learns by default?
Which is the correct description of optimal routing election for each protocol in the following options?( Radio).
An existing router running BGP, HW1, has both IBGP neighbors and EBGP neighbors configured on the router. Are the IP Neighbors and EBGP Neighbors described below correctly?
In an HWIP multicast network, where multiple sources exist and each source has several receivers, which protocol allows source-to-RP traffic and RP-to-receiver traffic to share the same tree 2?
The BSR/RP mechanism described below describes the correct determination ?( Multiple choice questions).
There can be multiple C-BSRs in the
In an intra-domain MPLSVPN network, when a packet enters the public network and is forwarded, it is encapsulated with two layers of MPLS tags, and the description of the two layers of tags in the following options is incorrect
The following description of the attributes of BGP is correct?( Single choice questions).
In the description of the MAC address spoofing attack, the error is ? Radio
Regarding route introduction, what is the following description of the error?
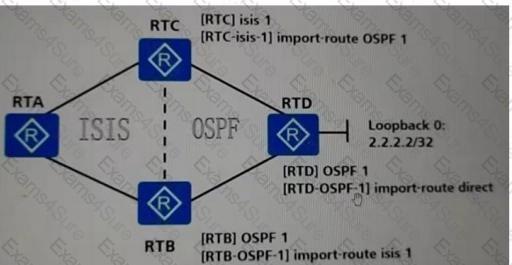
In a network, the same gigabit running S and OSPF anti-tampering and fluttering as shown in the figure, on the two border routers RTB and RTC are introduced into the wine route, the device question is to use gigabit one port strobe, , 222 The network is introduced into the OSE via impotrote direct on the RTD, assuming that all other configurations are dead default configurations, then the description of this network is wrong ?
As shown in the figure, the neighbor relationship between R1 and R2 has just been established, and the database synchronization process between R1 and R2 is correct.

If a DR needs to be elected between multicast routers running PIM-SM to be responsible for the sending and receiving of source or member multicast data, which one is described correctly below for the DR election rule?
In RSTP , which port provides a backup path to reach the root node of the spanning tree? What state is the port in?
A switch joins a running stacking system after powering up, a behavior known as heap overlay.
Regarding the description of the security level of the configured firewall security zone, the error is ?
Compared to IPV4 multicast, which of the following descriptions is the characteristic of IP6 multicast?
The switch uses IPSG technology to verify the source address of the IP packet, and the verification matrix used by the IPSG is obtained through the ARP resolution process in the listening network
As shown in the figure, the use of redundant links between the branch and the headquarters to establish IPsecVPN, while turning on URLPF on the Router_B for traffic from branch l, which of the following options is correct?

In EPIM-SM, the following description of the PIM Join message is correct?
APIM Join messages are sent every 3 minutes, and status
B.
PIM Join messages for the multicast tree are only sent when the multicast tree is first establishedC.
The PIM Join message is sent every 60 seconds to refresh the status of the upstream router mroute for the multicast treeD.
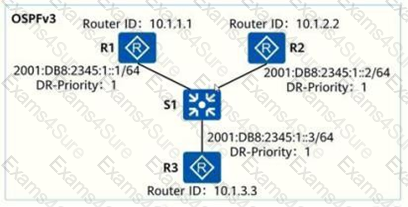
The upstream router sends a PIM Join acknowledgment in response to each PIM Join message received from the downstream routerOSPFV is the GP running on the P4 network) OSPF3 is the KGP running on the IP6 network. OsPFV works the same basic way as OSPF2, such as elections for DR and BDR. As shown in the figure, an engineer uses three routers for IP6 service testing, and he wants to interconnect the IPv6 network by running OSPFv3 Which of the following statements is correct regarding the election of the network DR?
?BGP4+?,Update ????M IP_R EACH_NLRI ?????next hop network address ????? ?
In cross-domain VPN-OptionB packet forwarding, two ASBRs exchange the same LSP tags once.
As shown in the figure, R1, R2, and R3 run OSPP at the same time and declare their respective ring ports, as described below is the error.
When judging the old and new LSA, the serial number parameter and the age parameter are used , and the following two parameters are correct for ?( Multiple choice questions).
A When the router receives two LSAs, where the sequence number is the same and the checksum is the same, the smaller the age, the better
B.
When the router receives—The age of the LSA is set to 3600S, the LSA is unavailableC.
If the serial number of the LSA reaches the end value of Ox7FFFFFFF, the current router advertises an LSA with an age of 3600SD.
Both the serial number and age parameters can determine whether the LSA is old or new, and the router prioritizes the sequence to participate in the teaching, and the larger the betterIf the OSPP protocol is running in the network , after configuring the non-backbone area in the OSPP area as the Totally Stub region, the ABR router sends a message to Totally. The Stub region issues an LSA with an LS ID of 0000, and what type of LSA is the LAS to?
Users hope to be able to make the router forward and select messages according to their own defined policies on the basis of traditional route forwarding, and can adopt policy routing, and the following description of policy routing is incorrect
In a shared network, what mechanism does PIM-SM use to prevent duplicate traffic?( Single choice questions).
S-4S supports multi-instance and multi-process, that is, on an IS-IS router, multiple VPN instances can be configured to associate with multiple IS-S processes, the following description of IS-IS multi-instance and multi-process, which are correct ?
Regarding the LDP protocol session establishment process, the description is correct?
In order to study the working mechanism of the OSPFv3 protocol, a project to build a network topology is as follows, the configuration of R1 and R2 is as follows, please ask the LSA switched between R1 and R2 What are the types?


TESTED 28 Apr 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.