CyberArk CDE Recertification
Last Update 2 days ago
Total Questions : 207
CyberArk CDE Recertification is stable now with all latest exam questions are added 2 days ago. Incorporating PAM-CDE-RECERT practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the CyberArk CDE Recertification exam format, identifying knowledge gaps, applying theoretical knowledge in CyberArk practical scenarios, you are setting yourself up for success. PAM-CDE-RECERT exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
PAM-CDE-RECERT exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through PAM-CDE-RECERT dumps allows you to practice pacing yourself, ensuring that you can complete all CyberArk CDE Recertification exam questions within the allotted time frame without sacrificing accuracy.
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA Hardening.ps1 perform when run?
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
You have been asked to design the number of PVWAs a customer must deploy. The customer has three data centers with a distributed vault in each, requires high availability, and wants to use all vaults, at all times. How many PVWAs does the customer need?
Which certificate type do you need to configure the vault for LDAP over SSL?
You have been asked to configure SNMP remote monitoring for your organization's Vault servers. In the PARAgent.ini, which parameter specifies the destination of the Vault SNMP Traps?
Which of the Following can be configured in the Master Poky? Choose all that apply.
Which of the following components can be used to create a tape backup of the Vault?
You are installing HTML5 gateway on a Linux host using the RPM provided. After installing the Tomcat webapp, what is the next step in the installation process?
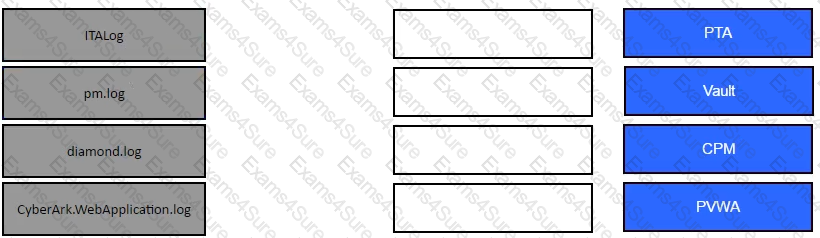
Match the log file name with the CyberArk Component that generates the log.
An auditor initiates a live monitoring session to PSM server to view an ongoing live session. When the auditor’s machine makes an RDP connection the PSM server, which user will be used?
Which components can connect to a satellite Vault in distributed Vault architecture?
You are installing multiple PVWAs behind a load balancer. Which statement is correct?
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
Which of the following Privileged Session Management (PSM) solutions support live monitoring of active sessions?
When running a “Privileged Accounts Inventory” Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
An auditor needs to login to the PSM in order to live monitor an active session. Which user ID is used to establish the RDP connection to the PSM server?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
Which report could show all accounts that are past their expiration dates?
Which of the following files must be created or configured m order to run Password Upload Utility? Select all that apply.
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will help the CyberArk Support Team debug the issue? (Choose three.)
Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
You are logging into CyberArk as the Master user to recover an orphaned safe.
Which items are required to log in as Master?


TESTED 18 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.