CyberArk Defender - PAM
Last Update 2 days ago
Total Questions : 239
CyberArk Defender - PAM is stable now with all latest exam questions are added 2 days ago. Incorporating PAM-DEF practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the CyberArk Defender - PAM exam format, identifying knowledge gaps, applying theoretical knowledge in CyberArk practical scenarios, you are setting yourself up for success. PAM-DEF exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
PAM-DEF exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through PAM-DEF dumps allows you to practice pacing yourself, ensuring that you can complete all CyberArk Defender - PAM exam questions within the allotted time frame without sacrificing accuracy.
You are creating a shared safe for the help desk.
What must be considered regarding the naming convention?
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault?
Your organization requires all passwords be rotated every 90 days.
Where can you set this regulatory requirement?
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
Which utilities could you use to change debugging levels on the vault without having to restart the vault. Select all that apply.
A Simple Mail Transfer Protocol (SMTP) integration is critical for monitoring Vault activity and facilitating workflow processes, such as Dual Control.
To manage automated onboarding rules, a CyberArk user must be a member of which group?
A Vault Administrator team member can log in to CyberArk, but for some reason, is not given Vault Admin rights.
Where can you check to verify that the Vault Admins directory mapping points to the correct AD group?
The Vault administrator can change the Vault license by uploading the new license to the system Safe.
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
Target account platforms can be restricted to accounts that are stored m specific Safes using the Allowed Safes property.
When Dual Control is enabled a user must first submit a request in the Password Vault Web Access (PVWA) and receive approval before being able to launch a secure connection via PSM for Windows (previously known as RDP Proxy).
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
All of your Unix root passwords are stored in the safe UnixRoot. Dual control is enabled for some of the accounts in that safe. The members of the AD group UnixAdmins need to be able to use the show, copy, and connect buttons on those passwords at any time without confirmation. The members of the AD group Operations Staff need to be able to use the show, copy and connect buttons on those passwords on an emergency basis, but only with the approval of a member of Operations Managers never need to be able to use the show, copy or connect buttons themselves.
Which safe permission do you need to grant Operations Staff? Check all that apply.
You are onboarding an account that is not supported out of the box.
What should you do first to obtain a platform to import?
You are logging into CyberArk as the Master user to recover an orphaned safe.
Which items are required to log in as Master?
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
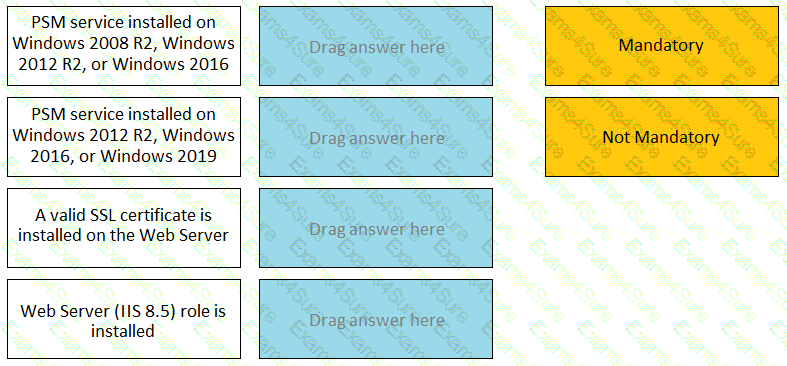
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
You are creating a Dual Control workflow for a team’s safe.
Which safe permissions must you grant to the Approvers group?
In your organization the “click to connect” button is not active by default.
How can this feature be activated?
Which certificate type do you need to configure the vault for LDAP over SSL?
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission.
Where do you update this permission for all auditors?
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?


TESTED 06 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.