Trend Micro Certified Professional for Deep Security Exam
Last Update 3 days ago
Total Questions : 80
Trend Micro Certified Professional for Deep Security Exam is stable now with all latest exam questions are added 3 days ago. Incorporating Deep-Security-Professional practice exam questions into your study plan is more than just a preparation strategy.
By familiarizing yourself with the Trend Micro Certified Professional for Deep Security Exam exam format, identifying knowledge gaps, applying theoretical knowledge in Trend Micro practical scenarios, you are setting yourself up for success. Deep-Security-Professional exam dumps provide a realistic preview, helping you to adapt your preparation strategy accordingly.
Deep-Security-Professional exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through Deep-Security-Professional dumps allows you to practice pacing yourself, ensuring that you can complete all Trend Micro Certified Professional for Deep Security Exam exam questions within the allotted time frame without sacrificing accuracy.
Which of the following operations makes use of the Intrusion Prevention Protection Module?
Based on the following exhibit, what behavior would you expect for the Application Control Protection Module?
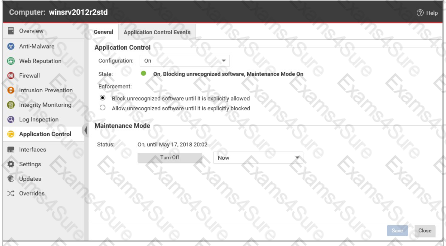
As the administrator in a multi-tenant environment, you would like to monitor the usage of security services by tenants? Which of the following are valid methods for monitoring the usage of the system by the tenants?
Your organization stores PDF and Microsoft Office files within the SAP Netweaver platform and requires these documents to be scanned for malware. Which Deep Security component is required to satisfy this requirement?
A collection of servers protected by Deep Security do not have Internet access. How can Smart Scan be used on these computers.
New servers are added to the Computers list in Deep Security Manager Web config by running a Discover operation. What behavior can you expect for newly discovered computers?
Which of the following correctly identifies the order of the steps used by the Web Reputation Protection Module to determine if access to a web site should be allowed?
Your organization would like to implement a mechanism to alert administrators when files on a protected servers are modified or tampered with. Which Deep Security Protection Module should you enable to provide this functionality?
Which of the following correctly describes the Firewall rule Action of Force Allow?
The Firewall Protection Module is enabled on a server through the computer details. What is default behavior of the Firewall if no rules are yet applied?
Based on the configuration setting highlighted in the exhibit, what behavior can be expected during a malware scan?
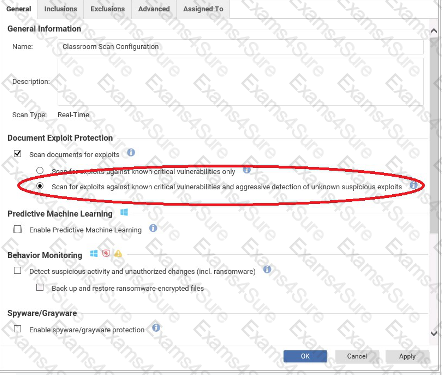
Which of the following statements correctly identifies the purpose of the Integrity Monitoring Protection Module?


TESTED 19 May 2024
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.