Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI)
Last Update 4 days ago
Total Questions : 630
Dive into our fully updated and stable 300-410 practice test platform, featuring all the latest CCNP Enterprise exam questions added this week. Our preparation tool is more than just a Cisco study aid; it's a strategic advantage.
Our free CCNP Enterprise practice questions crafted to reflect the domains and difficulty of the actual exam. The detailed rationales explain the 'why' behind each answer, reinforcing key concepts about 300-410. Use this test to pinpoint which areas you need to focus your study on.
Refer to the exhibit.
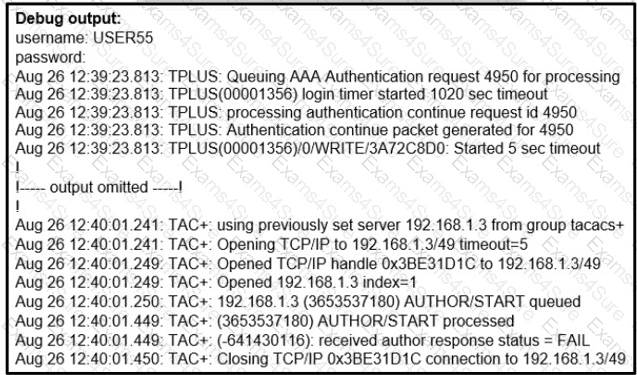
A network administrator logs into the router using TACACS+ username and password credentials, but the administrator cannot run any privileged commands Which action resolves the issue?
Exhibit:
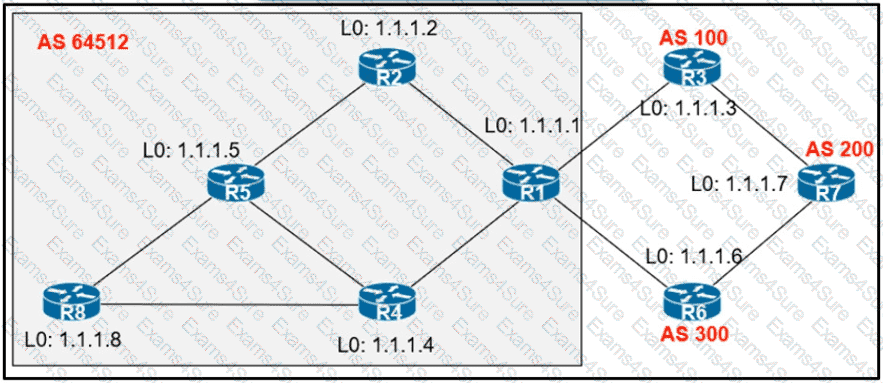
An engineer configured R2 and R5 as route reflectors and noticed that not all routes are sent to R1 to advertise to the eBGP peers. Which iBGP routers must be configured as route reflectors to advertise all routes to restore reachability across all networks?
An engineer configured a Cisco router to send reliable and encrypted notifications for any events to the management server. It was noticed that the notification messages are reliable but not encrypted. Which action resolves the issue?
Refer to the exhibit.
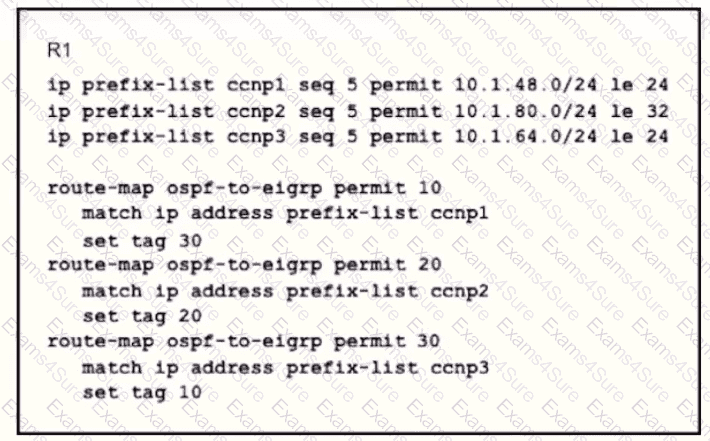
An engineer wanted to set a tag of 30 to route 10 1.80.65/32 but it failed How is the issue fixed?
Refer to the exhibit.
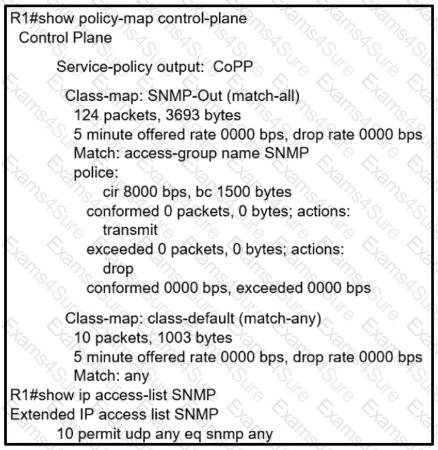
R1 is being monitored using SNMP and monitoring devices are getting only partial information. What action should be taken to resolve this issue?
What is the minimum time gap required by the local system before putting a BFD control packet on the wire?
Which Ipv6 first-hop security feature helps to minimize denial of service attacks?
Refer to the exhibit.
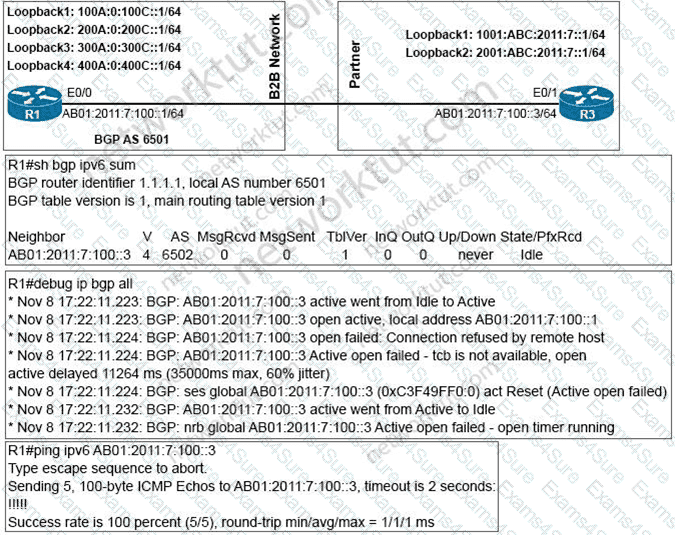
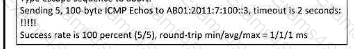
An engineer configured BGP between routers R1 and R3 The BOP peers cannot establish neighbor adjacency to be able to exchange routes. Which configuration resolves this issue?
Refer to the exhibit.
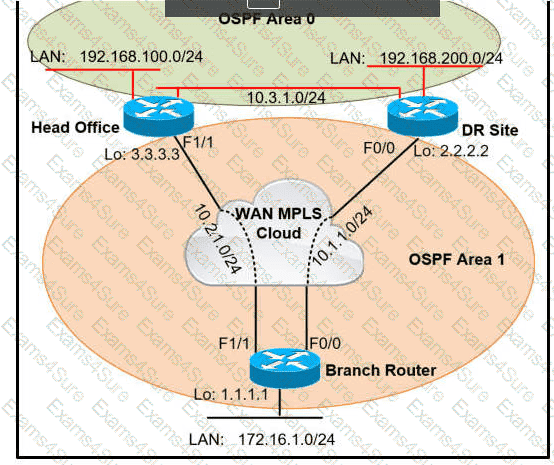
A network administrator reviews the branch router console log to troubleshoot the OSPF adjacency issue with the DR router. Which action resolves this issue?
Refer to Exhibit:
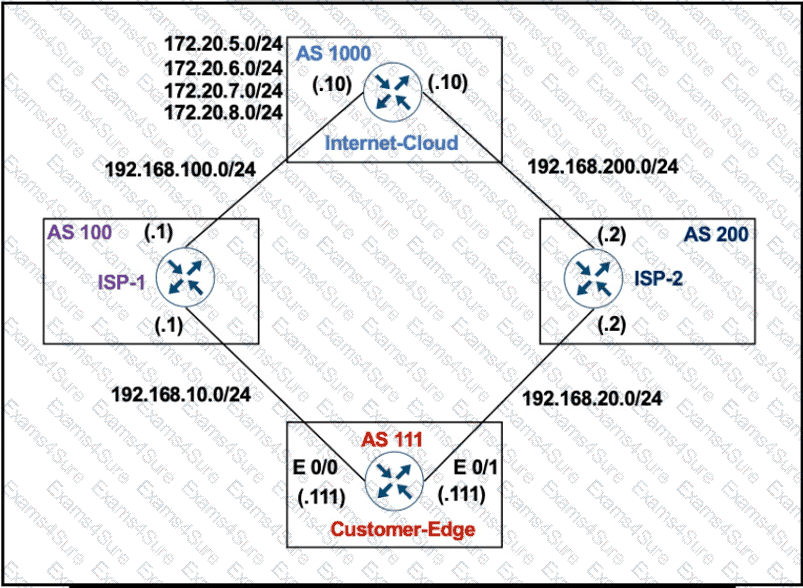
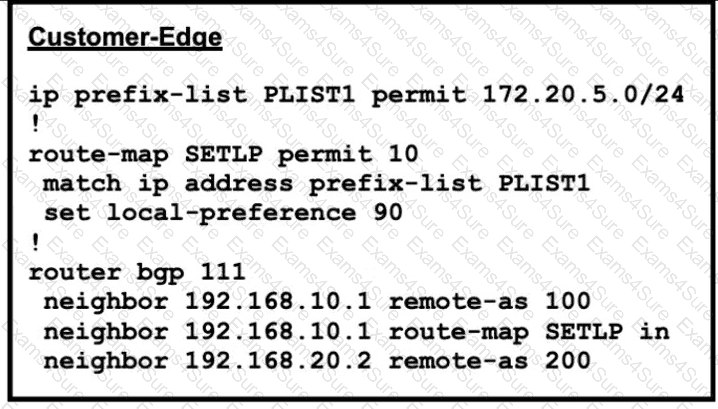
AS 111 wanted to use AS 200 as the preferred path for 172.20.5.0/24 and AS 100 as the backup. After the configuration, AS 100 is not used for any other routes. Which configuration resolves the issue?
Refer to the exhibit.
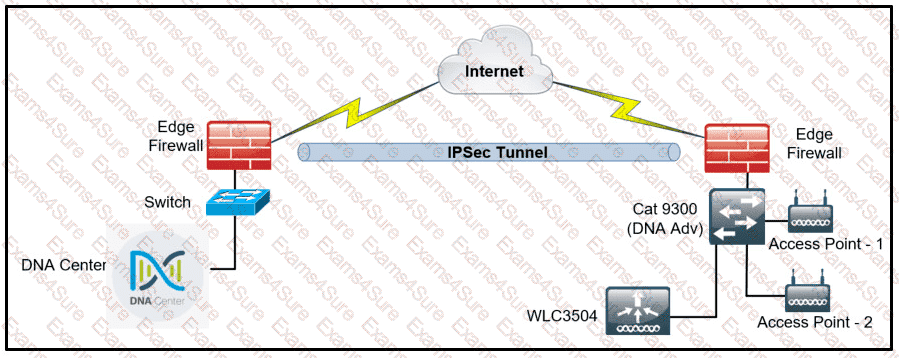
A network administrator is discovering a Cisco Catalyst 9300 and a Cisco WLC 3504 in Cisco DNA Center. The Catalyst 9300 is added successfully However the WLC is showing [ error "uncontactable" when the administrator tries to add it in Cisco DNA Center. Which action discovers WLC in Cisco DNA Center successfully?
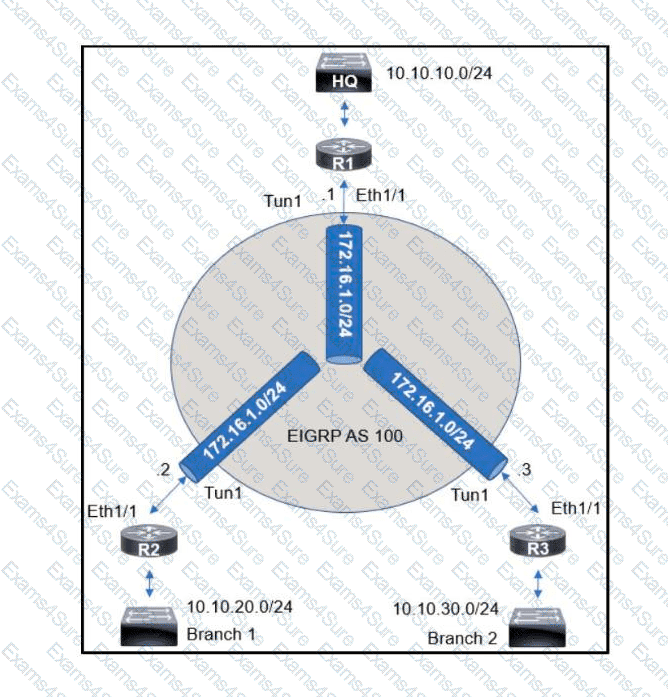
An engineer sets up a DMVPN connection to connect branch 1 and branch 2 to HQ branch 1 and branch 2 cannot communicate with each other. Which change must be made to resolve this issue?



TESTED 04 Mar 2026
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.